
It employs garlic routing and encryption, with dark web sites denoted by the .i2p suffix. All you need to do is visit the Tor browser webpage and click the Windows icon, leading to the installation process. The Windows process is simple and requires you to allow or toggle certain settings. It has market-leading encryption, AES-256-bit encryption, a no-logs policy, and RAM-only servers. Based in Panama, the service has independently audited its privacy policy using PwC twice.
Are Dark Web Apps Illegal?
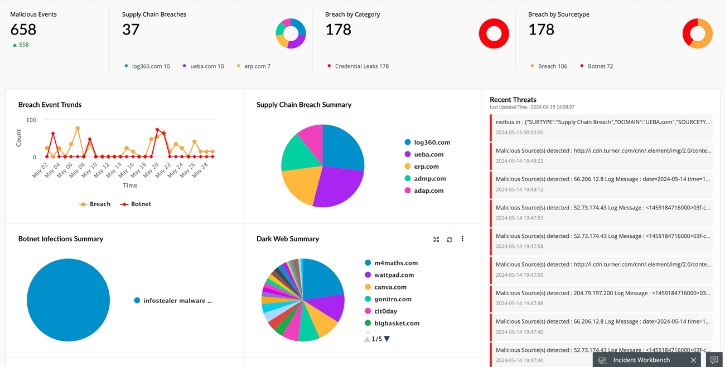
Remember to follow the safety measures we discussed, such as keeping your device and software updated, using strong passwords, and practicing good browsing habits. Trust your instincts and exercise caution when interacting with Dark Web websites and content. A Dark Web scanner is a tool used to search the dark web, a part of the internet not indexed by standard search engines, for information such as personal data or credentials. These scanners help individuals and organizations detect if their sensitive information has been exposed or traded on the dark web.
How To Install Tails OS
The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. Since you’ve now installed the Tor browser, you can safely browse dark web websites and other (previously) hidden websites. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s.
Using Onion Browser
Websites on the Dark Web use unconventional top-level domains like .onion, which cannot be accessed using regular browsers. A VPN adds that extra layer of privacy you need when browsing the dark web on Tor. Tor hides your IP address by routing your traffic through multiple encrypted layers, but that’s only in the Tor network. Your ISP (Internet Service Provider) or anyone monitoring your connection, like a network administrator, can still see you’re accessing the dark web. A dark web browser is a specialized tool that enables users to access the “dark web”—an encrypted, private network that hosts websites not indexed by mainstream search engines. Unlike the surface web, which we access daily through browsers like Chrome and Firefox, the dark web requires specific browsers to maintain user anonymity and ensure secure access.
- In summary, while dark web apps provide unique functionalities and can enhance privacy and freedom, they must be approached with caution and informed understanding.
- Antivirus is a great way to stay protected while using the Tor browser or the dark web.
- Furthermore, deanonymization may be possible as a result of browser flaws.
- The dark web goes deeper, requiring special browsers and configurations to access hidden sites and services.
- From this point onwards, you can enjoy complete anonymity and security while being able to access “.onion” websites and other dark web browser domains.
Best (Free) TOR Browser With VPN

Open the Downloads folder on your Mac, and double-click the file you just downloaded. Simply visit the Tor Project website, then click on the “Download Tor Browser” button found in the upper right-hand corner or the center of the web page. The browser uses a unique security system, which the United States Navy originally developed to protect the government’s intelligence communications. The Tor Browser does have its flaws, which we’ll go into a bit later. However, there is an easy-to-use way around that, which we’ll talk about later. Experienced blogger with a strong focus on technology, currently advancing towards a career in IT Security Analysis.
As a general rule, it’s best to use the default settings in Tor or the Onion Browser. Changing any of the default settings can make websites misbehave or not load correctly. A VPN also helps protect you from risks in the Tor network itself.
Governments worldwide have intensified online surveillance in the name of national security, while corporations increasingly monetize personal data. As digital rights erode, anonymity online is becoming a necessity rather than a luxury for many individuals. If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details.
How To Install The Tor Browser On All Linux-based Devices
Yes, Dark Theme (aka Dark Mode) is available in all modern versions of Microsoft Outlook including the classic desktop application for Windows and Mac, the new Outlook, web and mobile apps. One of our favorite VPN providers is ExpressVPN; grab an ExpressVPN subscription using our link and receive three months extra FREE. The first few alpha versions of the official Android Tor Browser required the Orbot app to route traffic through the Tor network. However, the most recent versions can now route the traffic through Tor without Orbot. The developer, Masum Islam, indicated that the app’s privacy practices may include handling of data as described below. When you run Tor Browser for the first time, you will see the option to connect directly to the Tor network, or to configure Tor Browser for your connection.
From what I have seen, it behaves the same way that the PC Tor Browser does, offering many of the same features, security and anonymity. Of the many Tor browsers for iOS I have tried, Onion Browser tales the cake. Knowing that The Tor Project endorses Onion Browser is a huge step forward for Tor use on iOS and mobile platforms I general.
A Free App For Android, By Looklikeaydn
Hacking techniques are rapidly evolving, and the hacking business is booming. Hackers don’t always attack companies and individuals to use the breached data themselves. They can sell that stolen information on the dark web to other scammers and criminals.
Download Norton 360 Standard For Windows—Complete Cybersecurity For Your PC

Since each node server in the Tor network is volunteer-operated, you never know who operates the relays that your data is traveling through. While this isn’t an issue for most of the trip (since each relay only has access to the previous and next relays in the network), it is an issue with the exit node. All of this keeps the sender anonymous thanks to how each intermediary node only knows the location of the previous and next node. So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers. There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game.
If you decide to venture into the dark web, be sure to educate yourself on the potential risks and dangers. Make sure you install and run strong security software on your computer and devices to help ensure the privacy and security of your data. Get Norton 360 Deluxe to help protect the personal data you send and receive online. Similarly, they determine the specific interests of visitors’ navigation and present appropriate content. For example, they prevent the same advertisement from being shown again to the visitor in a short period.
- That means that only 0.024% of all the known pages are findable in Google’s search engine.
- Users should prioritize safety and legality while navigating this hidden part of the internet.
- For example, you might tell your closest friend about a problem in your personal life, but you would not tell the clerk at your grocery store.
- Using a dark web app for illegal activities can put you at risk of legal consequences.
- All you need to do is visit the Tor browser webpage and click the Windows icon, leading to the installation process.
- The dark web is part of the deep web, which includes web pages that don’t appear in standard search engine results.
Identity Guard Pricing
Afterwards, your request will be matched with the appropriate website. Tricky, but effective; that’s why it’s, by far, the best method to access dark web content. In this guide, we have discussed the steps you can take to access the Dark Web on your Android device.
Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple types of nefarious goods and services, including weapons and identity fraud resources. While many dark marketplaces have been shut down by authorities, new ones soon appear in their place. Internet users can surf the dark web anonymously thanks to specialized darknet browsers.
That’s a trick question, because there isn’t even a good free VPN, much less a best VPN. Freebie VPNs will track their users’ online usage, as they make money by selling this tracking info to advertisers and other nosy parties. We’ve found that Tor is an excellent way to keep your internet browser-based online activities undercover, although we’ve also seen how using the Tor Browser can bring unwanted attention.



