The U.S. Army developed “onion routing” to protect intelligence communications online. You’ll need directories and search engines designed for .onion domains. As long as you are vigilant about your online activity, there aren’t any issues. The maximum trouble you can get into on the dark web is visiting political forums or marketplaces. In that case, the government might flag and monitor you even if you’re not a participant or trader. Therefore, to access the deep web, you need passwords to those databases.
Should You Use A VPN And Tor?
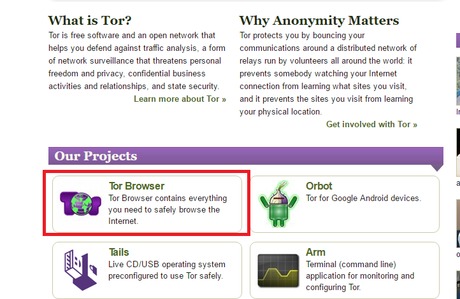
You’ll know you’re on the dark web when the URLs end in “.onion” — these addresses only work inside the Tor network. The deep web refers to anything that search engines can’t crawl.1 These pages aren’t public — not because they’re illegal, but because they require a login or special access. Think of your email inbox, banking dashboard, cloud documents, subscription content, or internal business tools. As an information security architect with over 10 years advising Fortune 500 companies on privacy technologies, I‘ve helped thousands of clients securely leverage the dark web. This comprehensive guide will equip you to safely access and navigate Tor hidden services. All dark web sites are hosted through the dark net, and nearly all of their traffic is encrypted.
This app connects to the Tor network, allowing you to visit .onion sites. His work empowers journalists, researchers, and privacy advocates to safely access unindexed content. Syed’s expertise stems from hands-on testing of tools like Ahmia, NotEvil, and Haystak, coupled with a rigorous commitment to operational security.
Ethical Guidelines For Responsible Monitoring
- The dark web contains a wide range of content, including forums, marketplaces, and websites offering various services.
- So before accessing any dark web site, you must weigh substantial risks.
- The dark web is full of malware, phishing scams, and other malicious threats that can compromise your device and personal data.
- Sometimes, a dark web user on any of its open forums can also attempt a phishing attack to steal your personal information and further use it for financial gains or identity theft.
- In 2024, I used Haystak’s premium tier for an article on dark web marketplaces.
The Dark Web remains a shrouded corner of the internet—an enigmatic space where privacy, free speech, criminality, and censorship resistance intersect. Navigating the Dark Web can be a complex endeavor, but you don’t have to do it alone. Reputable organizations, security researchers, and privacy advocates provide a wealth of insights, tutorials, and software to help you explore safely and responsibly. Below are some trustworthy starting points and authoritative references. I2P is an anonymous overlay network designed primarily for peer-to-peer applications. There are many different ways to access the dark web, but navigating it can be tricky and dangerous if you don’t know what you’re doing.
Legal Trouble
Therefore, you should select a VPN service that does not save traffic logs containing metadata like your IP address. If you are a journalist or whistleblower and want to access the dark net for legal purposes, this guide is for you. Successfully navigating this hidden world requires preparation, vigilance, and a thorough understanding of both the technical and ethical challenges at play. From choosing the right networks and privacy tools to avoiding scams and malicious software, every step you take should be guided by caution and informed judgment.
- Relays help route traffic securely by passing encrypted data through multiple nodes before reaching its destination.
- While some legitimate uses exist on the dark web, it is also known for hosting illegal activities such as drug trafficking, weapons sales, and more.
- It describes how Tor anonymizes users by routing traffic through different servers.
- Seek recommendations from reliable sources, such as trusted online communities or forums dedicated to privacy and security.
What Is The Best Dark Web Search Engine For Beginners In 2025?
Setting up Tor correctly is critical if you want to browse the dark web without exposing your real identity. A single misstep, like skipping a leak test or using the wrong browser, can undo all your privacy efforts. Accessing the Tor network through Tails OS (The Amnesic Incognito Live System) on a thumb drive is a highly secure way to browse the dark web anonymously. Tails is a portable operating system specifically designed for privacy, and it includes the Tor Browser by default. Here’s a step-by-step guide to setting up Tails on a USB thumb drive and using it to access Tor.
How Do Onion Routing And Tor Work?
Antivirus will ensure that any viruses or malware downloaded from the dark web are removed. Tor routes your traffic through a chain of relays to obscure your IP address. This makes it harder for websites, ISPs, or surveillance tools to see who you are or what you’re doing. Many sites on the dark web are scams, and some host illegal content. Hosting a website on the dark web isn’t just for people with nefarious intentions. With the right setup, it can offer immense privacy and security benefits.
When making purchases on the Dark Web, evaluate sellers and their products carefully. Read reviews, check ratings, and be cautious of scams or fraudulent activities. Securely make payments using cryptocurrencies like Bitcoin, and maintain anonymity throughout the process.
Follow Us
By following these steps, you can ensure a higher level of anonymity when making payments on the Dark Web. However, it is important to note that no method is foolproof, and remaining cautious and vigilant is key to protecting your privacy. While the Dark Web offers users a certain level of anonymity, there have been instances where user data has been compromised and exposed. This puts individuals at risk of being targeted by criminals or having their sensitive information sold to third parties.
In an attempt to stop criminal organizations operating on the dark web, authorities are setting up fake websites to track possible criminal activity. By doing this, they get access to whoever is visiting the sites — including you if you accidentally end up there. In some parts of the world, simply using a browser like Tor can get you flagged by these agencies, even if you don’t partake in illegal activity.
Attempting to even view these can be illegal in many countries and states, so stay well clear of them if you want to keep a clean record and conscience. While researching these markets might be exciting, it is critical to take caution and avoid engaging in unlawful activity. We provided a step-by-step guide on how to access the Dark Web securely, emphasizing the use of a VPN and the Tor Browser. We also highlighted the importance of understanding onion websites and navigating the Dark Web safely. While we discourage engaging in illegal activities, there are legitimate websites and forums on the Dark Web that promote privacy, cybersecurity, and digital rights. These include platforms dedicated to whistleblowing, secure communication, and privacy advocacy.
Best Deep Web Browsers For Safe Access
Start with verified .onion links and Tor’s “Safest” mode to avoid pitfalls. Filtered engines (Ahmia, NotEvil) and directories (Torlinks) minimize dangers, while unfiltered tools (Torch, Haystak) require expertise. Balancing these trade-offs with robust security ensures safe, ethical exploration. In 2025, NotEvil helped me find a privacy tool safely, but a risky marketplace link slipped through, avoided only by verification.
Adopt proactive dark-web monitoring today—it’s one of the most valuable investments your business can make to safeguard its future. By consistently implementing these best practices, your organization can significantly reduce the risk of future data breaches, safeguarding your assets, reputation, and stakeholder trust. Effectively managing data leaks begins with accurately identifying compromised information and quickly assessing the potential impact. The following practical guidelines outline how businesses can pinpoint breaches and determine their severity and urgency.
These marketplaces operate using cryptocurrencies like Bitcoin to ensure anonymity in financial transactions. Without a VPN, the first server in the Tor network (the entry node) can see your real IP address, and your internet service provider (ISP) can see that you’re accessing the dark web. This creates a privacy risk even if they can’t see what you’re doing on the dark web.
Most dark web sites are unregulated, which means that there are fewer mechanisms in place to prevent you from accidentally downloading malware. Identifying specific individuals who use the dark web can be quite tricky. However, we advise connecting to one of our recommended VPN services to stay anonymous.



