
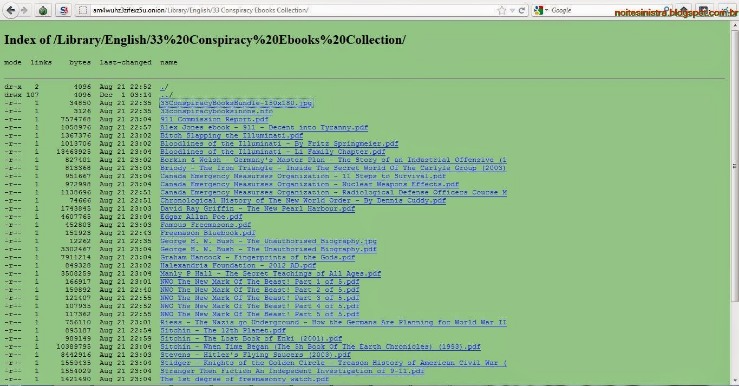
The Imperial Library currently holds around 1.5 million books, some of which may be hosted illegally, and thus, their consumption might violate copyright laws. To protect yourself against any legal repercussions, you should consider using NordVPN. Therefore, you will always find updated search results while using this service. Proton also offers other security tools besides ProtonMail, such as Proton Drive, Proton Pass, Proton Calendar, and Proton VPN.
Journalist in India → Uses Tor to access a whistleblowing portal → Submits information anonymously while protecting their identity. This blog offers a complete guide on how to access the Dark Web using the Tor Browser, along with step-by-step instructions, security tips, legal warnings, and real-world examples. Not Evil works more like a regular internet search and is the successor to TorSearch (another Tor search engine) and the Evil Wiki (another listing site).
Are Dark Web Search Engines Legal?
We check all v3 Onion links before we add them, and remove fraudulent items on a regular basis. This site contains the very best onion links you can find anywhere. The dark web is often confused with the deep web, but they are not the same.

Can I Search The Dark Web From My Phone?
While there are many great Linux distributions to work with, Qubes should be high on your list if you value privacy. Qubes is a leading Linux-based operating system, well known for privacy. Apart from Tails OS, Qubes allows the highest secure connectivity for virtual machine systems.
Whistleblower platforms enable confidential document submission without compromising the identity of sources. GlobaLeaks is an open-source platform designed for NGOs and media to create customizable submission portals, emphasizing decentralization and anonymity. StrongBox adds advanced metadata stripping and encrypted messaging features, increasing whistleblower protection.
Use The Tor Browser
The service emphasizes privacy with zero-knowledge encryption and no registration requirements. My tests showed reliable performance for smaller files, but larger transfers can be slow due to Tor’s limitations. Pitch is a dark web-based Twitter/X alternative, providing a secure platform for anonymous discussions and information sharing. Unlike many dark web platforms, it maintains strict content guidelines while protecting user privacy.
Step-by-Step Guide: How To Access The Dark Web Using Tor Browser
You can access thousands of issues, from the most popular to the most niche. It is one of the best sites on the dark web to find your favorite comics. In addition, its technology is open-source, and it doesn’t keep your data, which proves it is safe to use. In addition, you can connect your Keybase account with X, GitHub, or Reddit to let people easily trust that they are talking to the actual person. Also, the platform has a feature of automatic deletion of messages – set a timer and they will be deleted after a set period.
Dangerous Software
Simply put, onion sites are websites that are hosted on the Tor darknet that use the “.onion” top-level domain instead of “.com,” or “.gov” for example. All Onion sites use The Onion Router (Tor) protocol to encrypt the user’s connections. It’s only possible to access onion sites through the Tor browser or by setting up some special network configurations. ProPublica was the first online publication to win a Pulitzer prize. They were also the first to host a .onion site to make their content accessible to everyone everywhere, regardless of censorship or anti-journalist laws in certain countries. SecureDrop is a really awesome Tor service that can be used to share information without revealing your identity.
Other Hidden Sites
Thankfully, there are effective measures that keep you secure on the dark web and ensure you remain protected and anonymous while accessing .onion sites. Using a reliable VPN with Tor provides a way to improve security when accessing dark web links. The VPN encrypts your traffic before it enters the Tor network, preventing your ISP from seeing that you’re using Tor.
Its operations focus on respecting user privacy and maintaining anonymity through the use of the Tor network. The dark web is a double-edged sword, offering anonymity but also posing significant risks. It’s a hub for illicit activities, with cybercriminals ready to exploit any weakness. Without the right precautions, your IP address could be exposed, leaving you vulnerable to hacking, tracking, or even identity theft.
Is It Illegal To Visit And Use Dark Websites?
Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn’t know exactly what you’re doing. Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS. The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now).
- This makes them a safer (though still not foolproof) option for searching the Dark Web.
- TorLinks serves as a backup or secondary directory site to the popular Hidden Wiki.
- Many directories are outdated or cloned, while others include malicious .onion addresses.
- The developers of ProtonMail recommend using the Tor browser to visit the dark web version of the service.
- Your ISP, and possibly the authorities, may decide to start monitoring your activity more closely to look for threats or illegal activity.
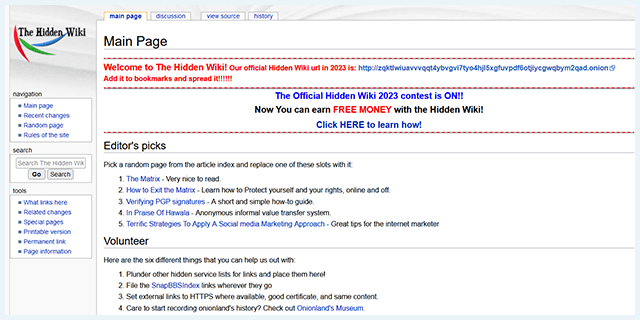
These platforms underpin the technical infrastructure necessary for dark web functionality. Another critical advantage of the Hidden Wiki lies in its resistance to censorship. This makes it an essential resource for users living under oppressive regimes or in countries with strict internet controls. The Hidden Wiki empowers people to access alternative viewpoints, engage in uncensored discussions, and exercise freedom of information that surface web search engines cannot guarantee.

This repository contains a comprehensive list of .onion links to various resources available on the dark web. The links are organized into categories such as general resources, marketplaces, and email services. This collection aims to provide users with a broad overview of available dark web resources. ZeroBin allows users to post encrypted text that even the host server can’t read — perfect for pasting links or messages securely. OnionShare lets users share files directly from their device over a temporary .onion address without needing a centralized server. These tools are open-source, regularly audited, and trusted by privacy communities around the world.
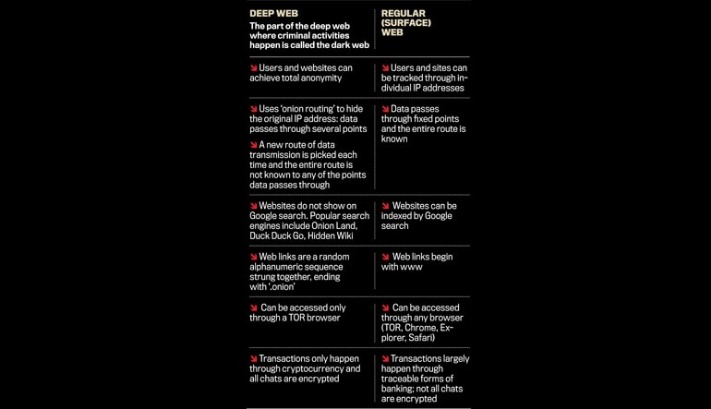
Most dark web links are hosted on “.onion” domains due to the sensitive nature of the businesses or services they host. Tor websites may provide secure access to cryptocurrency wallets and anonymous email clients, and they’re also used to access black market sites. In the image above, (a) is the surface web, which includes publicly visible websites like blogs, shopping sites, and news sites. (b) is the deep web, which consists of sites that require a login to access like email accounts, banking portals, and subscription services. And (c) is the dark web, which is the part of the deep web that isn’t indexed by search engines and requires special tools like Tor Browser to access.
The deep web is made up of email platforms, workplace portals, subscription services, and banking websites — basically anything that requires a login. The “surface web,” on the other hand, is the publicly available part of the internet that search engines index. This repository provides a curated collection of educational and legal onion links, along with guides and resources on how to access the dark web securely and protect your privacy. The ProtonMail Onion site offers the same encrypted email services trusted globally, now accessible anonymously through Tor. This service protects messages from interception and censorship, critical for journalists and activists.



