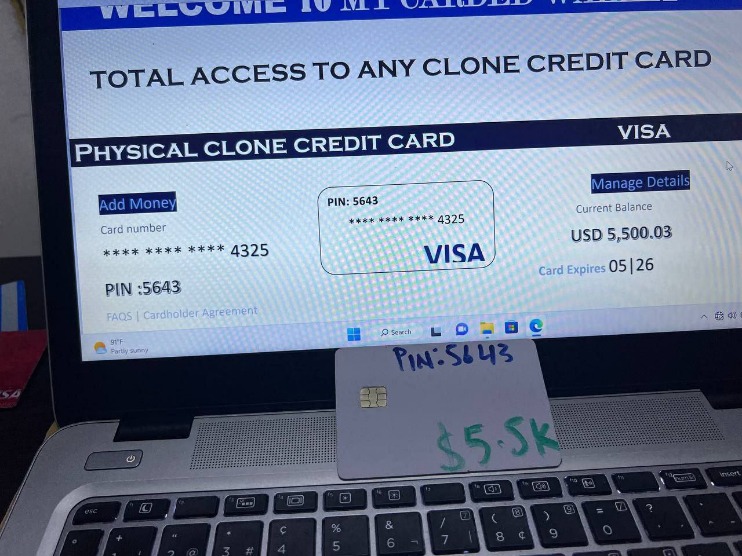
The more secure your information is, the less likely it will be to fall into the hands of a threat actor. Once they had access to the victim’s account info, scammers would estimate their wealth to gauge the types of purchases they could make with the card. The first leak offered only the information contained in magnetic stripes of compromised cards, while the latest sale includes fullz – card number, expiration date, CVV/CVC, cardholder name, and extra personal info. The three suspects from Indonesia confessed to stealing payment card data using the GetBilling JS-sniffer family. The cards were likely compromised online, using phishing, malware, or JavaScript-sniffers, which are increasingly popular among cybercriminals.
Microsoft Authenticator Requests Exporting Passwords Before July
Check your FICO Score 8 and TransUnion credit report on the go with CreditWise’s secure biometric login. Plus, take advantage of all the tools at your disposal—like the Credit Simulator and dark web alerts.To download the CreditWise app on mobile devices, scan the QR code to launch either the Google Play Store or the iOS App Store. Check your credit score, TransUnion® credit report and more for free— all without hurting your credit score. Your lender or insurer may use a different FICO® Score than FICO® Score 8, or another type of credit score altogether.

Best Credit Monitoring Services Of 2025
It has built a reputation for being a reliable source of stolen credit card data and PII. Renowned for its extensive inventory of financial data and sophisticated operating methods, Brian’s Club is a key player in the underground economy of financial cybercrime. If you use your credit card for work-related purchases, you should monitor for exposure to prevent fraud and protect your financial security.
Collecting Threat Intelligence

A 2018 special report from Vice shows an anonymous scammer browsing stolen credit card numbers on the dark web. He chooses one, stamps the number and information onto a blank card, and uses that card to make payments, often using the stolen payment information to buy goods, like gaming systems, and sell those as well. This article will explore credit card theft on the dark web, explain how criminals obtain and use stolen data, and explain how to detect and prevent credit card fraud. Strong passwords and security tools add extra layers of defense against cyber threats. Many tracker apps link directly to bank accounts for up-to-the-minute info.

Using Alerts For Unknown Tracker Alerts
- You could be liable for up to $50 if you take up to two business days, or up to $500 if you wait longer.
- Before submitting any personal information, look up the company through the Better Business Bureau (BBB) and read online reviews from current and past customers.
- If you have to make a purchase immediately, create a password-protected hotspot to connect to your phone’s cellular data instead.
- Every American is entitled to free credit reports from all three of the major credit bureaus each week by visiting AnnualCreditReport.com.
- Beginning in September 2021, Abacus Market has established itself as one of the leading dark web marketplaces.
- Payment information moves through a series of specialized dark web markets.
Much like the situation after Silk Road was taken down, out of the ashes of Joker’s Stash, we have seen dozens of new carding data providers crop up, some specializing in particular regions or types of card data. Digital banking has transformed both consumer banking and the threats posed to banks and their customers. In addition to new scams and schemes targeting online banking customers, we have seen the evolution of criminal marketplaces to trade in stolen information, stolen accounts, and stolen money. This has been a particularly interesting history of development around stolen payment card information.
The availability of the CreditWise tool and certain features in the tool depends on our ability to obtain your credit history from TransUnion and whether you have sufficient credit history to generate a FICO Score 8. Some monitoring and alerts may not be available to you if the information you enter at enrollment does not match the information in your credit file at (or you do not have a file at) one or more consumer reporting agencies. No one can prevent all identity theft or monitor all transactions effectively. Further, any testimonials on this website reflect experiences that are personal to those particular users, and may not necessarily be representative of all users of our products and/or services. We do not claim, and you should not assume, that all users will have the same experiences. A credit freeze limits access to your credit reports — preventing anyone from opening new accounts or taking out loans in your name.
The Top 7 Dark Web Marketplaces In 2025

Breachsense monitors the dark web, Telegram channels, hacker forums, and paste sites for external threats to your organization. These generated numbers link to your real card but can be limited by merchant, amount, or time. Early detection enables your security team to prevent a transaction, minimizing the risk of a chargeback. For example, requiring additional verification for purchases that deviate from a customer’s normal pattern, rather than forcing verification for every single transaction. Require multi-factor authentication for high-risk transactions, but it needs to be implemented intelligently.
The Industry-leading Password Manager For Work, Family, And Life
Free and paid tutorials on the dark web teach fledgling criminals how to use stolen credit cards. Make purchases with your debit card, and bank from almost anywhere by phone, tablet or computer and more than 15,000 ATMs and 5,000 branches. A breach on online marketplace eBay between late February and early March 2014 exposed sensitive personal information of an estimated 145 million user accounts. Cybercriminals gained access to eBay’s systems after compromising a small number of employee login credentials.
After the season ends, you will get Emblems based on your position. This season runs until September 27th 2025We have full details of the Ranked Match season, including points required for each rank in our Season A4a section. In Grand Theft Auto Online, players who purchase warehouses and garages for illicit cargo and stolen cars can buy/steal and sell them through trade on the “SecuroServ” syndicate website. Background research tasks included learning from past drug lords, researching legal matters, studying law enforcement agency tactics and obtaining legal representation.

Therefore, it’s better to minimize your digital footprint as much as possible to make yourself a less vulnerable target. For the strongest security, experts recommend using an authenticator app, like Okta or Google Authenticator, rather than receiving 2FA codes on your phone. This is because scammers can gain access to your phone number (and SMS texts) by conducting what’s called a SIM swapping scam. Jory MacKay is a writer and award-winning editor with over a decade of experience for online and print publications.
Responding To Detected Credit Card Fraud
Check how much Bitcoin you’ll receive and ensure the exchange rate meets your expectations before proceeding. If you have an outdated browser, your connection to CreditWise (and most other sites) might not be secure. We recommend that you update your browser to a version that supports 128-bit encryption and secure sockets layer version 3.0 or higher. For example, they might be able to figure out who your family members are and where you have accounts. They can use this information when they pretend to be an employee at a company or government agency. Once they take control of your number, they can have your text message MFA codes sent to a phone they control.
Dark Web Credit Card Numbers: Understanding The Risks And Fraud
Thieves often buy cards to use on specific sites that don’t have security features like Verified by Visa (VBV) or MasterCard’s SecureCode. These cards can be used to make purchases online or in-store, and can even be used to withdraw cash from ATMs. Use this guide to learn how to easily automate supply chain risk reports with Chat GPT and news data. “These precautions include keeping your devices fully up-to-date with any system updates as they are released, exploring the dark web via a reputable browser such as Tor, and using a VPN to protect yourself online. It is also worth regularly scanning your computer for viruses if any nasty programs slip past your firewalls. The most expensive card details, which cost about $20, were in Hong Kong and the Philippines and the cheapest, some at just $1, originated in Mexico, the US and Australia.



