Tor was designed to protect American intelligence communications online. Tor Browser has since become a popular tool of journalists, activists, and others that may be subject to being monitored online. There are several ways to protect your online activities from being tracked. Using a VPN is perhaps the easiest and most efficient way to protect your online travels from prying eyes, as it hides your real IP address, and encrypts all of your online traffic.
Tips For Staying Safe On The Dark Web
Well, as long as you don’t visit sites with underaged models or that engage in human tracking or that sell drugs and other illegal items. One of the major advantages of using Tor in overly-restrictive countries is that it keeps your online travels private. Unfortunately, some oppressive regimes have figured out a way to block Tor traffic. Tor Over VPN is when you first connect your computer or mobile device to your VPN service and then use the Tor Browser to travel the internet. When you install the Tor Browser, it comes preconfigured with the most secure privacy settings.

Risks Of Accessing The Dark Web:
While the surface and deep web can be accessed this way, the dark web requires special software. Tor (The Onion Router) is the most commonly used browser for the dark web; however, it’s also accessible through networks like Freenet, Riffle, and I2P. You can find both legal and illegal websites/activities on the dark web, as it isn’t regulated in any way. The dark web remains a mysterious part of the internet, offering both benefits and potential dangers.
MULTI-LAYERED ENCRYPTION
- Exploring the dark web can be eye-opening, but it’s also risky without the right protection.
- Let’s go through the setup process for each, as well as how to use them effectively.
- This protocol, a layer built atop the traditional internet layer, routes communication between random servers (called nodes or relays) to obscure the source.
- Like any other site of such nature, Awazon Market isn’t free from risks, so be careful while accessing it.
- Simply download the file, install the software, and you’re ready to use its web-based interface.
Also known as The Onion Router, TOR enables users to browse the Internet, including the Dark Web, anonymously. It bounces traffic through several servers before delivering it to its destination, making it harder to track a user’s activity or location. Hendrik is a writer at vpnMentor, specializing in VPN comparisons and user guides. Even in countries like the US and Europe where it’s legal, you may be put under surveillance for simply using a dark web browser like Tor. Authorities use the dark web as a tool to catch criminals participating in illegal activities such as human trafficking, drug or weapon deals, and more.
Step 3: Securely Connecting To The Network

If found, take immediate steps to secure your accounts and personal information. The dark web can certainly be dangerous — with no regulation, it’s a riskier place to hang out than the surface web. Malware and scams are scattered like landmines around the dark web. And with many unfamiliar-looking sites on the dark web, it’s harder to distinguish safe websites from shady ones, and easier to fall victim. Dark web domains tend to be inconsistent — new ones pop up and others disappear, which makes sense if they offer questionable or illegal goods and services. If you want to access the Tor network on your iPhone or iPad, you can use the Onion Browser app.
Step 2: Set Up Your Tools
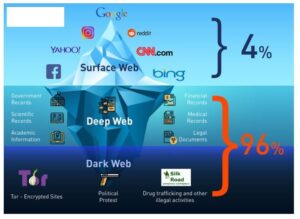
The dark web is a murky part of the internet that isn’t accessible via a normal browser — and can be dangerous to visit if you don’t know what you’re doing. We’ll show you how to access and browse dark web sites, and how using a VPN to encrypt your connection can help you visit the dark web more securely. The Dark Web’s cornerstone is built upon specialized anonymity networks and protocols that allow users to access hidden services without directly revealing their identity or location. Understanding the differences and capabilities of various anonymity tools will help you make informed decisions about which networks best serve your needs. Beyond the legal aspects, there are ethical considerations to weigh. At the same time, these networks can also facilitate exploitation, hate speech, and other harmful activities.
By default, Tor has stricter privacy settings than most standard web browsers. Users can take further steps to maximize privacy when browsing with Tor. To use a new circuit, click the circuit button next to the domain. Then, click on New Tor circuit for this site, as illustrated below.
Protecting Against Malware And Exploits
There are many more sites hidden away in a part of the internet called the deep web. Some of them (the hardest ones to access) are situated in what is known as the dark web. Infiltrations can put you at risk of monitoring for other types of activity as well. Evading government restrictions to explore new political ideologies can be an imprisonable offense in some countries. China uses what is known as the “Great Firewall” limit access to popular sites for this exact reason. The risk of being a visitor to this content could lead to being placed on a watchlist or immediate targeting for a jail sentence.
It is important to differentiate between the tool (Tor) and the actions performed using that tool. The dark web is legal in most countries, provided you do not engage in illegal activities. However, in countries with strict censorship laws — such as China, the UAE, and Pakistan — accessing the dark web is considered a crime. In Russia and India, authorities closely monitor dark web traffic. Before accessing the dark web, use a secure Tor VPN to hide your IP address and data from ISPs and potential malicious nodes on the dark web. You can download native VPN apps for different devices from its website or official app stores.
Use A VPN Or Proxy For An Extra Layer Of Security
Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). The best thing is to actually understand how to find the fresh, new links. Formerly known as Archive.is, it is one of the best onion sites on the dark web. It aims to preserve the internet’s scientific and cultural heritage. ProtonMail is a Swiss-based email service that is very easy to use. You are not required to provide your personal information to create an account.

Step 1: Install A VPN
A VPN enhances your anonymity by creating a private network from a public internet connection. It allows you to mask your location and obscures your online activities, making it more difficult for cybercriminals to track you. By using a VPN, you can prevent eavesdroppers from intercepting your data when you’re connected to public Wi-Fi or any unsecured network. You cannot access the dark web using regular browsers like Chrome, Edge, or Safari. You must use a secure web browser that prioritizes privacy and security and can access onion sites.
It’s a hidden layer of the internet, shrouded in secrecy, that you can’t access using traditional search engines like Google or Bing. Unlike the websites you browse daily, the dark web requires special tools to access and explore. It’s like a secret alleyway (say Diagon Alley from “Harry Potter”) in the sprawling city of the internet, known only to those who seek it out. As was mentioned previously, Tor entry nodes can still see your IP address. If you want to mitigate that possibility, downloading a VPN is the best way to do so – it funnels your traffic through a private server and keeps your IP address hidden.