
Each server adds a layer of encryption, and this layered system is what lends The Onion Router its name. This is also why the sites on the dark web are called Tor links. Using a VPN (Virtual Private Network) in tandem with the Tor browser ensures an added layer of security by encrypting your traffic before it reaches the Tor network.

Legitimate Use Cases For The Average User
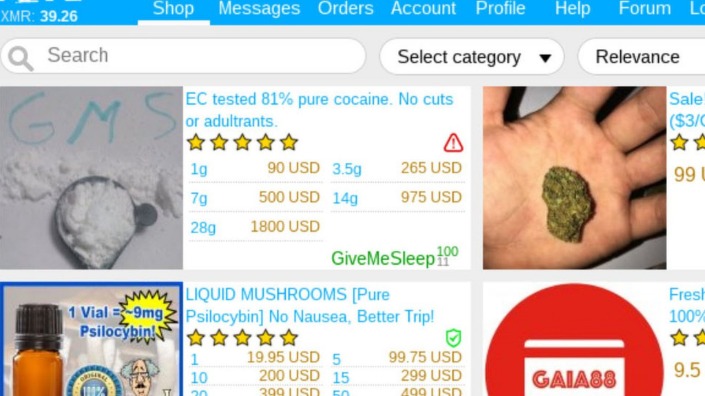
We strongly advise you against visiting it, even if your intentions are good. Knowing about various types of ransomware and common hacks can help you better prepare to spot cybersecurity threats on the dark web. However, if someone were to pursue this, here are some safety strategies. This market specialized in selling marijuana related products and magic mushrooms, with no “hard drugs” for sale. The Silk Road was the first popular DNM which appeared on the scene in back in 2011.
- There’s plenty of illegal content, products, and services available on the dark web.
- While the dark web is famously known as an illegal platform for criminal activities, that’s not all about this part of the web.
- Although it’s not inherently illegal to access the Dark Web, remember that certain sites and activities may be.
- He was arrested in a San Francisco library while logged in as site admin.
- It’s extremely rare and only useful in very specific cases, like if your VPN is only accessible through Tor.
Comparative Table: Browsers
The Tor browser is open-source and is used to access the dark web, where data is encrypted and routed through multiple relays before reaching its destination. The dark web isn’t indexed by regular search engines and is known as a hotbed of criminal activity. While that’s sometimes true, it can also be used for ethical purposes. TOR Browser is a free, modified version of the Firefox web browser configured to connect to the TOR network.
Cybersecurity Best Practices For Protecting Your Digital Assets
In a way, it feels more like a private club than an open market, and that’s exactly how the operators want it. The tool can of course also be used to surf the internet anonymously without criminal intent. To do this, click on “Connect” in the “Connect to Tor” dialogue. You cannot simply carry out a normal Google search on the darknet. You need a darknet search engine like Torch, Ahmia, and Haystack, or a directory like the Hidden Wiki. Darknet users often use the Tor browser for Windows to access it.
Remember that any website engaging in illegal activities such as drug trafficking, weapons sales, hacking, and human trafficking violates international laws and, therefore, is illegal. Anonymity on the dark web may be attractive to government critics and victims of harm who want to keep their identities private. However, criminals and malicious hackers also use the dark web to hide their illegal activities.
- It does support whistleblowers by offering them anonymity and secure communication in an oppressive regime.
- Also, some toxic chemicals are peddled on the dark web that may cause severe damage to the targets.
- Although PrivateVPN has what sounds like a true no-logs policy, it has yet to be independently audited.
- Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails.
- In fact, create new throwaway accounts and documents if possible.
Official Websites And Documentation
You may also use it to access the regular internet more anonymously. LifeLock Standard helps safeguard your personal information, accounts, and identity. Social media platforms like Facebook and news sites like the BBC and ProPublica have also waded into the dark web’s waters.
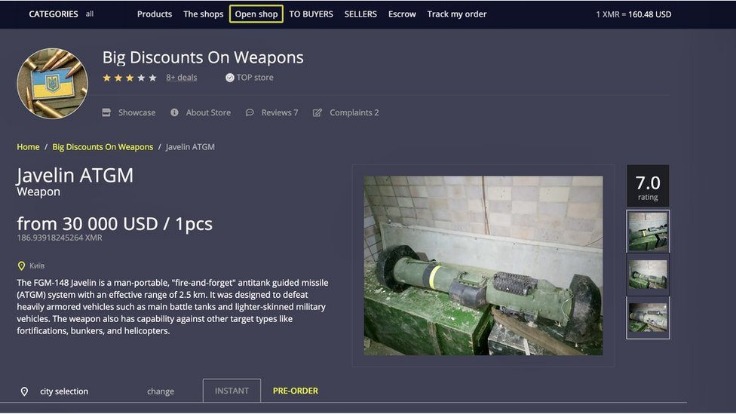
What Services And Tools Are Available On The Dark Web?
Though not entirely shoddy, the dark web has a reputation for hosting illegal activities. It does support whistleblowers by offering them anonymity and secure communication in an oppressive regime. But navigating the dark web is full of cybersecurity and legal challenges. Though it is not illegal to visit the dark web, accessing it can expose you to serious legal risks, even if you don’t have any criminal activity in mind.
It will normally take a while to connect because Tor — unlike other browsers — will route your traffic through different nodes. You should also keep in mind that overall speeds will likely be impacted; for example, a page might take a few seconds longer to load than what you are used to. The Tor network is operated by thousands of volunteers worldwide who maintain the proxy servers that protect your identity. You can download the Tor Browser for Windows, MacOS, Linux, and Android. ZDNET tested the best VPNs available based on speed, number of servers, security features, price, and more. ExpressVPN is our pick for the best VPN overall, thanks to its fast and reliable connection and the wide range of platforms it works on.
Cybersecurity Course Fees A Complete Guide To Costs, Certifications
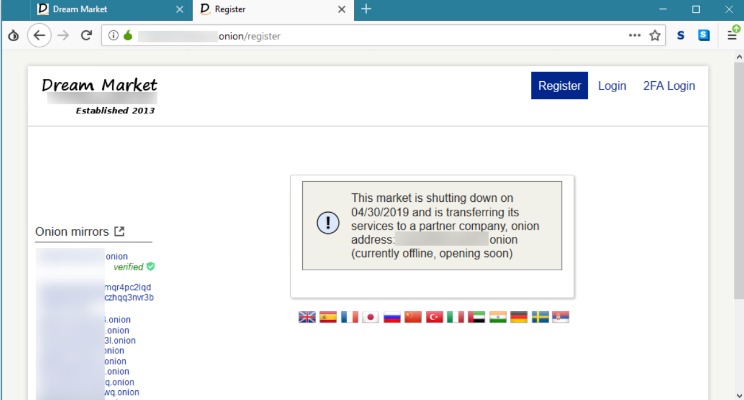
In 2008, the Tor Browser was released, which made it easy for anyone to get on the darknet. The existence of an anonymous and hidden internet then allowed for alternative information channels and illegal websites to flourish. In 2002, the dark web grew significantly when researchers supported by the US Naval Research Laboratory built and released the Tor network.
Risks Of Accessing The Dark Web:
The invisible web is made up of data and information that is not indexed and cannot be searched for by using traditional search engines. It includes media and archives which cannot be crawled and indexed with current search engine technology. The dark web is a part of the internet that isn’t indexed by search engines. You’ve no doubt heard talk of the “dark web” as a hotbed of criminal activity — and it is. Researchers Daniel Moore and Thomas Rid of King’s College in London classified the contents of 2,723 live dark web sites over a five-week period in 2015 and found that 57% host illicit material.
The biggest and most frustrating part about dark websites is that they live for a short span of time. These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites.
We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. Therefore, the legality of the dark web will mainly depend on how you use it. You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom.
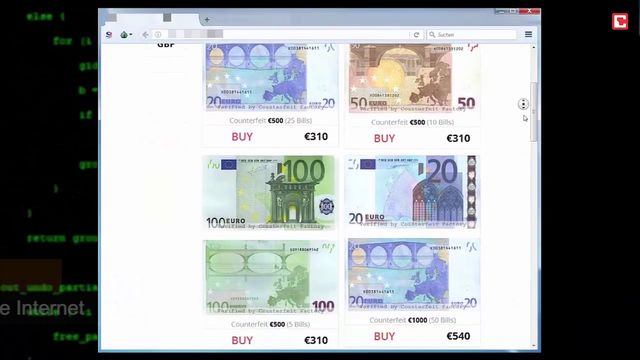
Adhering to these methods will help you safely locate legitimate resources while minimizing exposure to potentially dangerous or fraudulent sites on the Dark Web. Fake marketplaces and scams thrive on the dark web because there’s no one to turn to if you get scammed. For example, randomly clicking a link can land you in extreme content, such as child pornography, which is a serious criminal offense to access.



