This lack of indexing is intentional on the part of many service providers, as it helps to protect private information. On the other hand, the dark web uses darknets like Tor, Freenet, Riffle or other anonymized and encrypted networks as the underlying technology. These networks live on the fringes of the hidden web, offering many layers of encryption to protect data in transit.
How To Access The Deep Web Safely?
To access this, one must have a working Internet connection and will also require a search engine (such as Google, Bing, etc.) to access the content. For example, in 2016, investigative news outlet ProPublica launched a hidden version of its website on the dark web to provide a secure and anonymous way for readers to access its content. This initiative aimed to protect the privacy of individuals in repressive regimes or those concerned about surveillance, allowing them to read news without exposing their identity. No, you cannot access the dark web through a regular browser, like Google Chrome, Firefox, etc.

Are There Legitimate Uses For The Dark Web?
- Besides, some additional protective measures may include application sandboxing, erase-on-shutdown, etc., based on a particular OS.
- It is even tougher for the law enforcement to monitor anonymizing networks like Tor.
- This network ensures that each user’s privacy and identity are locked down tighter than Fort Knox, using layers of encryption that bounce your connection across the globe.
- Besides the illegal activities on the Dark Web, political dissidents and privacy advocates also use it for anonymity.
- The dark web isn’t all illicit deals and seedy undertakings; it’s used for an array of purposes.
While it is not always possible to discover directly a specific web server’s content so that it may be indexed, a site potentially can be accessed indirectly (due to computer vulnerabilities). First off, let’s get this out the way – the Deep Web is more than 99% of the internet, and it’s not synonymous with the Dark Web. Moreover, the anonymity that protects users can also be a double-edged sword. In stark contrast, the Dark Web can only be accessed using specialized software like the Tor browser. These aren’t hidden for nefarious reasons, but rather to protect sensitive or personal information.
Tor Vs VPN – What’s The Difference?
Interestingly, at the cusp of the new millennium by the US Naval Research Laboratory originally developed the Tor project. An early version of the Tor browser was created to combat the challenges presented by the lack of privacy during the initial days of the internet. Its main goal was to prevent spy communications from being discovered; however, the framework was eventually repurposed and made public. The tools to carry out the cyberattack may have been bought off a dark web marketplace, but the attacker would propagate the attack using mediums available on the standard web (such as email or chat).
Safety Measures And Precautions To Take
Most of the internet is divided up into restricted pockets known as the deep web. On the other hand, the deep web is that hidden part of the internet, which is personal and open to its respective owners. For instance, Harvard University received a bomb threat via a disposable email in December 2013. They immediately informed the FBI, which singled out all the campus students using Tor in that time frame. Finally, one of them, Eldo Kim, confessed to using Tor and Guerrilla Mail to send bomb threats to the university authorities to postpone the exams. Ideally, you should have a separate anonymous identity for each substantial outing on the dark web.
The deep web is the part of the internet you can’t access through search engines like Google and Bing. Also referred to as “non-indexed” content, it’s any content hidden behind some kind of access control such as a log-in or code word. It contains 7,500 terabytes of information, compared to only 19 terabytes of information in the “surface” web. To look at it differently, it makes up between 90% and 95% of the internet. Although the Dark Web is often used for illegal activities, it’s not illegal to access it in many countries.
The Dark Web first emerged with the creation of Freenet in the early 2000s. Freenet was designed to allow peer-to-peer, anonymous communication to protect against censorship. The Onion Router (TOR) technology used by the TOR browser and the Dark Web was created by a project funded by the US Naval Research Lab (NRL). The goal of TOR was to allow secure communication by intelligence sources in dangerous environments and has since been adopted by the general public for secure, anonymous browsing.
What Are Examples Of Deep Web Resources?
With that said, here’s all you need to know about the dark web, the deep web, and their differences. The Deep Web hosts everything behind a login or paywall—email, personal data, cloud data, medical records, etc. It’s mostly legit and secure, meant for day-to-day use without suspicion. You’ll find everything from your email inbox to private databases and paywalled content here.
Challenges To Finding Dark Web Sites
Two terms Darknet and Deep Web, in some sense, justify the presence of this hidden web about which most people are unaware. And those who know about the darknet often confuse it with deep web. Dimitri graduated with a degree in electronic and computing before moving into IT and has been helping people with their IT issues for the last 8 years.
Examples Of Deep Web Content:
All this can be easily avoided if you take safety measures when browsing the deep web to ensure your private accounts aren’t compromised. The risks of accessing the Dark Web include exposure to illegal content, potential scams, malware, and legal repercussions if one inadvertently engages in illicit activities. The dark web is a subset of the deep web that requires special software, like the Tor browser, to access. Known for its focus on anonymity, the dark web is often linked to illegal activities, although it also serves as a platform for privacy advocates and journalists in repressive regimes.
- The deep Web essentially contains databases and private networks that require special credentials to access it, while the Dark Web is specifically hidden, so only specific browsers like Tor can access these.
- The dark web has numerous legitimate uses but is still home to various criminal activities.
- However, the main caveat is that the Tor network (an onion network that uses a series of nodes to provide you with access) is very slow.
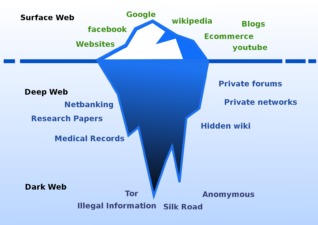
- When you’re Googling recipes or checking the news, you’re on the Surface Web.
- Phishing sites or malware can be used to gain access to your login credentials potentially leading to data theft or account takeover.
- The next layer is the “deep web,” a large invisible portion of the Internet.
The Dark Web Provides More Layers Of Encryption
On the other hand, the dark web is a small subset of the deep web that uses encryption to stay hidden from the surface web. It operates through a purposely obfuscated system of relay servers. These “entry nodes” keep users anonymous while browsing dark web websites. Company data that businesses store internally to manage operations and consumer data from inputted forms belong to the deep web. This data may include passwords, billing information, or purchase history—accessible to the user upon logging in but hidden from everyone else.
For starters, they both exist to offer people a higher degree of privacy than what is available on the surface web. The deep web is mostly used to store confidential information that would be vulnerable if easily accessible on the surface web. So unless you have the correct login details for certain information on the deep web, it can’t be accessed. This is great because you can have peace of mind knowing that sensitive data — like your medical information or internet banking profile — is safe. Surface web is that part of the Internet that has information related to sites that have been indexed by search engines.