The dark web is a part of the internet that isn’t indexed by search engines. You’ve no doubt heard talk of the “dark web” as a hotbed of criminal activity — and it is. Researchers Daniel Moore and Thomas Rid of King’s College in London classified the contents of 2,723 live dark web sites over a five-week period in 2015 and found that 57% host illicit material. Tor offers secure and encrypted access to the dark web forums, ensuring that the user’s IP address is hidden and difficult to trace. Therefore, cybercriminals use these forums because they offer assured anonymity and security. Perhaps one of the major attraction factors of these forums is undoubtedly anonymity.
While there may be legitimate uses and valuable information available, it’s essential to be aware of the potential risks and adhere to ethical behavior while exploring the hidden corners of the internet. By following these setup instructions, you can ensure a smooth installation and configuration process, allowing you to reap the benefits of Tor Browser and browse the internet anonymously. Uninstalling Tor Browser is as easy as deleting it and emptying your recycle bin. Some people get confused when trying to uninstall Tor, since it doesn’t show up in system programs. Tor does not make any changes to the Windows Registry, so don’t worry about leaving a trace after you uninstall your Tor Browser.
- Then, click on New Tor circuit for this site, as illustrated below.
- Here’s everything you need to know about this other internet, as well as how to access it.
- The browser uses a unique security system, which the United States Navy originally developed to protect the government’s intelligence communications.
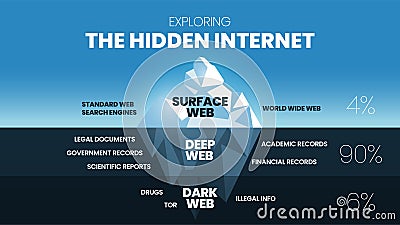
- Anyone can access the dark web, and it’s not that complicated to do so.
- Use directories like The Hidden Wiki or Dark.fail, which list verified and regularly updated onion links.
Download & Install The Tor Browser
The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web.
FAQs On Dark Web Links
This is why I strongly suggest using a Virtual Private Network to protect and enhance all of your online activities. A VPN keeps all of your online activities – including your web browsing, online gaming, streaming, and file-sharing – undercover and safe from being tracked or recorded. Another reason you don’t want to use the Tor Browser for your daily web browsing is that it draws attention to you. The Tor Browser prevents your ISP from seeing what websites you’re visiting, but it does not prevent the ISP from seeing that you’re using Tor. As I mentioned previously, using the Tor Browser will slow down your browsing. Since your traffic goes through a series of relays, getting encrypted or decrypted along the way, things slow way down.
Quick Comparison Table: The Dark Web Search Engine Features
Because of the relaying of data through the onion nodes, and the encrypting and decrypting taking place at each node, your internet connection will slow considerably. This means the Tor Browser is not recommended for streaming video, playing games, or downloading large files. VPNs are often recommended as protection in such cases, but Whited disagrees. The dark web refers to websites that are not on the regular internet but are instead hidden in a private network that is only accessible using specialized web browsers, such as the Tor Browser. Furthermore, it is strongly recommended to avoid downloading any files from the dark web unless absolutely certain of their safety and origin.

What Is Netiquette? 11 Online Etiquette Rules

If you want to use Tor privately, you can use either a VPN or Tor Bridges (Tor nodes that are not publicly indexed). Tor users in the USA, in particular, may want to use a VPN, which will be faster and more reliable. Journalists and whistleblowers, including Edward Snowden himself, often use the dark web and Tor to exchange sensitive information.
Will Visiting The Dark Web Attract Attention?
A common inquiry from Tor users is if they should use a VPN to add an extra layer of protection. To make things simpler, HTTP stands for Hyper Text Transfer Protocol, and this protocol governs communication on the world wide web. It’s what enables web browsers and servers to share information, including web pages and media files. Tor doesn’t support plugins because they introduce security risks. Malicious actors often target browser plugins to steal website credentials or install malware on unsuspecting devices, so Tor sidesteps these risks altogether.
HTTPS-only
Use the tips below to patch common blind spots and avoid easy-to-make mistakes. Avoid fraudulent Tor-like browsers that compromise your online security. The browser is free to download and works on multiple operating systems.
- Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS.
- To get on the dark web, you need a browser built for the job, and the best in the business is Tor.
- It focuses on privacy, censorship resistance, and ensuring free access to content.
- These tools are quite advanced; they crawl these forums and provide alerts to users if they find any of their information found in the dark part of the internet.
- Download Tor Browser to experience real private browsing without tracking, surveillance, or censorship.
If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. You might often see news stories about criminal activity involving the dark web, and because of what’s happening in some corners of the dark web, it tends to put off law-abiding companies and users alike.
This process anonymizes your browsing not only to websites but also to your internet service provider and anyone trying to monitor your network traffic. The dark web presents various threats, including malicious software and computer viruses, posing risks to users’ systems and data security. Users also face the potential danger of government monitoring and surveillance — or scams and fraud, and other activities that can lead to financial loss and identity theft. Your safety on the dark web depends more on cautious browsing habits than any single security tool.
Is Tor Completely Anonymous?
Yes, you definitely need a VPN if you want to access the dark web on your phone. This is because the dark web is full of potentially dangerous content, and a VPN will help keep your identity and personal information safe. Without a VPN, you could be putting yourself at risk of being hacked or scammed. The dark web contains much of the internet’s illicit content, ranging from drug trafficking to child pornography sites. A VPN allows a user to encrypt all internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing. A VPN, in combination with Tor, further enhances the user’s security and anonymity.
ProtonMail is a Swiss-based email service that is very easy to use. You are not required to provide your personal information to create an account. The email service is available both on the surface and on the dark web. The goal of an anonymous and privacy network, Tor, is not to engage in the extensive collection of data. However, data is required for understanding, monitoring, and improving the network.
This search field allows you to perform regular, but now anonymized, web searches through DuckDuckGo’s Tor site. Once the file is downloaded, run it to launch the installer and follow the prompt until the Tor browser is installed. Upon selecting the button for your operating system, you will be prompted to download the installer, which you should save to a folder. Upon opening the Tor website, you will be presented with various download options for the operating systems that Tor supports, including Windows, macOS, Linux, and Android. We’re a nonprofit organization and rely on supporters like you to help us keep Tor robust and secure for millions of people worldwide.
The first step is to download and configure the Tor browser from its official website. The Tor browser is your gateway to the dark web, allowing you to access .onion sites anonymously. Though it is not illegal to visit the dark web, accessing it can expose you to serious legal risks, even if you don’t have any criminal activity in mind.
A Quick Guide On How To Use A VPN With Tor

Lewis points to the “first contact problem”, when an attacker spots when someone moves from non-private tools to private ones, noting it’s been used to identify whistleblowers. Remember, the Tor browser connects to the internet differently than regular browsers in an attempt to increase your anonymity online. Tor is a powerful tool for enhancing your online anonymity, but it’s not a complete privacy solution. Learn how to set it up, explore what it does best (and where it falls short), and discover why pairing it with a trusted VPN could give you stronger, layered protection against prying eyes.



