Darknets and dark markets present a multifaceted challenge to businesses and society as a whole. While these hidden networks can be used for legitimate purposes, they are equally significant as vectors for cybercrime and illicit activities. Of course, not all activity on the dark web is criminal, but such marketplaces are where a lot of illegal trade and money laundering happens. By relying on encryption, pseudo-anonymous currencies, and network-level anonymity, they create a false sense of safety, drawing in both buyers and sellers.

How To Access The Dark Web Safely
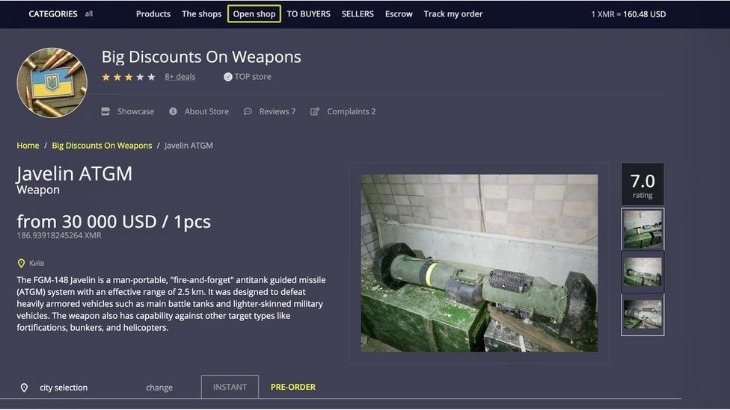
Darknet marketplaces emerged around 2011, with Silk Road setting the standard for how these platforms operate. Built on Tor, these sites mask IP addresses by routing traffic through encrypted relays, ensuring anonymity for both buyers and sellers. Bitcoin was initially used to process payments, offering pseudonymity rather than full anonymity. The darknet is a mysterious and often misunderstood part of the internet, attracting both intrigue and concern.
What Is A Darknet Market?
In panels (b, c), we show the number of all sellers and buyers per quarter, respectively. In panels (d, e), we show the median net income in USD of all sellers and buyers per quarter, respectively. In panels (f, g), we show the PDF of the total money received by each seller and the total money sent by each buyer, respectively. Content providers, especially those with eCommerce online shopping carts and other personally identifiable information, have perhaps an even more complex duty. Unknown vulnerabilities still pose a risk, but a good web security scanner can help reduce these.
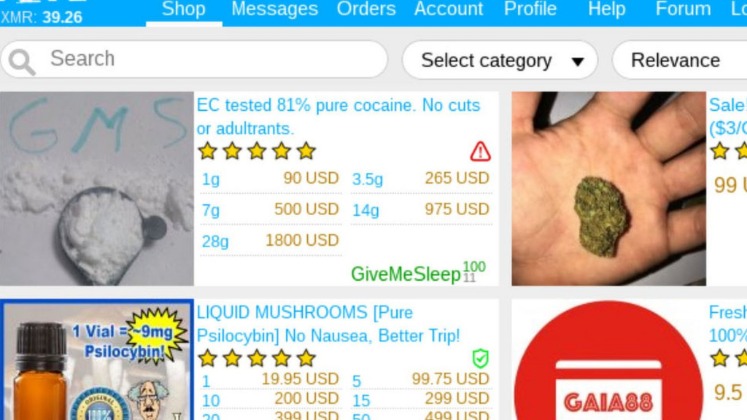
However, Bitcoin’s most important characteristic, and the thing that makes it different from conventional money, is that it is decentralized. This concept puts some people at ease because it means that a large bank cannot control its money. However, the money is untraceable, making it extremely valuable to black markets. What is surprising to many is the deep web is 90% of the entire web, which is full of unharmful and legal items – they’re just not indexed for search engines. The opposite term of the deep web is the surface web, which is the internet we use every day.
Acronis Cyber Protect Cloud: New Version C2505
- Part of what makes the dark web the dark web is that you can’t access it through your normal web browser, nor can you look something up on it via a Google search.
- You can access the black market by navigating to the right “.onion” addresses.
- Pirate Bay, a BitTorrent site that law enforcement officials have repeatedly shut down, is alive and well there.
- These sites cater to cybercriminals seeking valuable data, such as credit card numbers, login credentials, and personal information.
- Take control of your digital security with an exclusive demo of our powerful threat management platform.
For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”. For example, you can only find your Facebook friends, photos, and other information by logging into your Facebook account and finding the information there. On the deep web, you can find such “private” information on web pages.
Anonymity Through Tor
Shortly after the breach, a hacker group known as USDoD listed this data on dark web marketplaces, pricing it at a staggering $3.5 million. Don’t ever reveal your true identity on the dark web marketplaces because there’s a high chance of hackers and scammers misusing it. Beware of sharing your financial details on the dark web, as this can result in identity theft and your bank account amount being stolen. Mega Market is a new yet popular shop on the dark web that reached a skyrocketing reputation after the closure of the Hydra market. It allows you to buy and sell a wide range of products and services with a good user experience.
How Complex Are Dark Web Marketplaces Currently?
In fact, the attacker need not even have much of any technical prowess – just a basic, high-level, abstract understanding of web attacks. Simply install TOR, find the right .onion website, pay a little BTC, choose your target and attack (DDoS and email spam, of course, being the most common), and click a button. The guides and tutorials are so well documented that a Baby Boomer who has difficulty using their printer could reasonably perform these attacks. Whatever the risk involved, some users of the Internet felt that being told what they can and cannot possess, physical or digital, was akin to oppression. Telling someone they cannot do something is among the easiest ways to inspire them to do it.

Use Active Monitoring Of Financial And Identity Theft
But even with the odds seemingly stacked against it, the anonymity of the dark web can sometimes play to the law’s advantage. No ID and no location means you never really know who’s communicating with you. Tor stands for “the onion routing project.” It was developed by the U.S.
Use your common sense to steer clear of online scams and illegal activity. Online platforms allowed sellers to reach a global audience, significantly expanding the potential market for their goods and services. Enhanced anonymity and the use of secure payment methods reduced the risk of arrest for participants but also made it more challenging for law enforcement to track and prosecute illegal activities. These included back alleys, hidden storefronts, or even in plain sight at flea markets, depending on the goods or services being traded. Sellers and buyers faced significant risks, including arrest, theft, or violence, due to the illegal nature of their transactions and the lack of a secure environment.
HTTP Security Headers: An Easy Way To Harden Your Web Applications

In fact, previous studies on DWM transaction networks have revealed crucial aspects of the ecosystem13,14,15. However, they have so far mainly focused on DWM users, without distinguishing between buyers and sellers, and neglecting the different weight that more active users may have in the system. The reason is that the operational structure of DWMs inherently hides the seller–buyer link, as all transactions are made through the marketplace. Buyers send money to the marketplace, which in turn sends the money to the seller. In this article, we explore the evolution of the digital black market.
But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web. As mentioned before, your ISP and government institutions are not able to see what sites you visit on the Tor network, but they can probably see that you use Tor. The last thing you need to do is to start researching vendors and determine what marketplace is a possible vendor to buy the products from. Since you’ve now installed the Tor browser, you can safely browse dark web websites and other (previously) hidden websites. The same anonymity that publishers enjoy on the dark web can be utilized by users who want to read the available information.

At its peak, AlphaBay had over 400,000 users and facilitated transactions exceeding $1 billion. However, coordinated international law enforcement, including the U.S. Department of Justice (DOJ) and Europol, led to its seizure in 2017. With the increase of as-a-service models and do-it-yourself kits (with easy-to-use administration panels), anyone can create and use variants of similar malware. One can buy credentials, credit cards, and personally identifiable information without needing to be highly technical.
Is The Dark Web Getting Safer Or More Dangerous?
Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito. You can also find email messages, online bank statements, and much more information on the deep web – information that is usually private and inaccessible by the public on the surface web. The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web).



