
You now have a few best practices available to enhance your security and privacy when buying Bitcoin, and you can employ them with the following methods for more anonymity. You can use your judgment and capabilities to adopt at least a few to give you more peace of mind. After purchase, transfer your Bitcoin to a non-custodial wallet for more privacy. Cold storage, or hardware wallets, are preferred as they operate offline, reducing the risk of malicious attacks. Later efforts include Wasabi Wallet and Whirlpool from Samourai Wallet.
Cypher Marketplace
Yet, alongside the surface web exists a concealed domain known as the Dark Web, notorious for fostering illicit activities. Cryptocurrencies, notably Bitcoin, play a pivotal role in facilitating transactions within this covert network. In one of the most significant ransomware attacks in recent years, the DarkSide ransomware gang targeted the Colonial Pipeline, disrupting fuel supplies in the U.S. The attackers demanded a ransom of 75 Bitcoin (roughly $4.3 million at the time), which the company paid. However, law enforcement agencies, including the FBI, were able to trace the Bitcoin transactions using blockchain analysis tools. This led to the recovery of about $2.3 million of the ransom by tracking the movement of the cryptocurrency to wallets that were eventually linked to the attackers.
By using complex algorithms and multiple transactions, dark web bitcoin mixers create a tangled web of transactions, making it difficult to trace the origin and destination of the bitcoins. They essentially mix the bitcoins from multiple users and distribute them back to new addresses, obscuring the original source of the funds. This level of privacy and anonymity has made Bitcoin the currency of choice for many participants in dark web marketplaces. Its decentralized nature ensures that there is no central authority regulating or controlling the flow of funds. This means that transactions can take place without the interference or identification by governments or financial institutions.
Classification Of Sellers And Buyers
Never go to the dark web without mixed bitcoins, otherwise, there will be a record of your transactions which police can still search years later. These ‘onion layers’ assistance secure the client’s obscurity and give admittance to also ensured websites. These sites range from gatherings to wiki pages to sites and capacity much like clearnet sites. Dark Web areas every now and again use non-noteworthy, hashed URLs with the .onion high-level space. These sites block inbound traffic from all non-secure web associations.
Finding A Silk Road Alternative: What Are The Best Options Today?
This way, your traffic appears to be coming from those servers rather than your computer. As a rule of thumb, keep off from hosted wallets such as Coinbase wallet. Ideally, host your wallet locally by using Bitcoin clients such as Bitcoin Armory or Bitcoin-QT. Altcoin masking involves using anonymous altcoin as an intermediary to mask the Bitcoin transaction trail. With a decentralized exchange, this is unnecessary since there is no central authority to undertake the KYC process.
BloFin: High-Leverage Crypto Exchange With No KYC For Basic Trading
Another emerging technology that the dark web has adopted is blockchain. The decentralized and transparent nature of blockchain technology provides a level of trust and reliability for dark web users. With the rise of the dark web, a hidden part of the internet, users have been seeking ways to maintain their privacy and anonymity while using bitcoin.
- However, owing to the difficulty of identifying relevant transactions, most studies rely on user surveys17,18 and data scraped from DWM websites19,20,21,22,23,24.
- Cryptocurrencies like Bitcoin do not require account creation or linking with any personal information, which makes it easy for criminals to operate without worrying about revealing their identity.
- However, with the justification that authorities need to tackle money laundering, terrorism, and illicit operations, such a surveillant system may impact the smaller genuine retail investor heavily.
- Each bitcoin is divisible into 100,000,000 units, so you can purchase a fraction of a bitcoin that correlates with the precise value of your $ purchase.
Related Content
Privacy coins are incredibly difficult to trace, and although blockchain forensics companies advertise that they can trace some parts of ZEC transactions there is far less identifying information available. Monero, on the other hand, is incredibly difficult (impossible?) to trace (the IRS is even offering $625,000 to anyone who can crack monero). That said, one of the main takeaways from Chainalysis’ work is that the majority (~53%) of illicit transactions in crypto in 2021 were tied to scams and stolen funds. While those are serious problems, these are problems that are intrinsic to both crypto and legacy financial markets. Where there is money to be made there are false promises and stolen funds.
Non-custodial Bitcoin and Lightning wallet Blue Wallet added support for Payjoin at the end of 2020 to further enhance its wallet users’ privacy. Bitcoin developer Gregory Maxwell first developed CoinJoin in 2013, and early examples included Dark Wallet, JoinMarket, and SharedCoins. Joinmarket is still a leading project that allows users to create wallets and send coinjoin within the same application. Coin mixers are software and service solutions that allow users to mix their coins with others, disguising the ties between their addresses and real-world identity, thereby preserving their privacy.
Connecting To The Internet
These search engines work best if you already know what site you’re looking for, not for general browsing. One option is to try DuckDuckGo’s .onion version, which is great for privacy. Other options include Ahmia and NotEvil, which focus on listing .onion links. Hence, you never know when a popular .onion site is going to vanish, or even die. Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). The best thing is to actually understand how to find the fresh, new links.
There’s never too many kinds of investments that you can have, especially when you want to be a rising master of the game. If you’re unfamiliar with it, Bitcoin is a digital currency which only started within the last decade, so it’s not too late to be an early adopter. It has a bidding feature, with new batches of stolen data being frequently added. The Abacus Market links to the new dark web marketplace sections and took over much of the vacuum left by the AlphaBay takedown.
Bug bounties are motivators offered by numerous product designers and associations that reward you for discovering endeavors and weaknesses in their systems. Numerous Bitcoin trades and shared commercial centers offer projects like this to help improve their environments for their users. A master node is a committed job that monitors the blockchain progressively.

The Legality Of Accessing The Dark Web

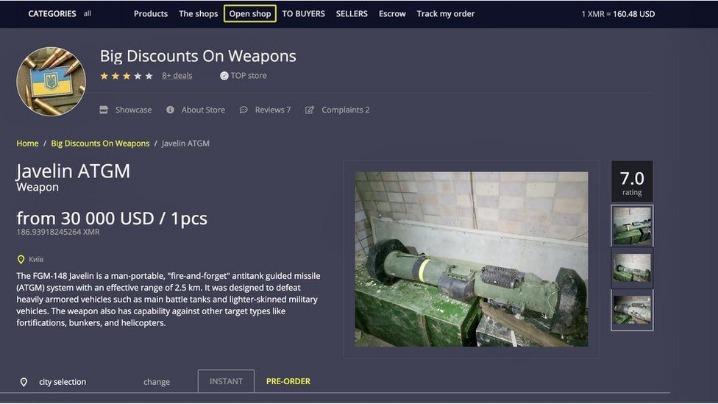
Users can conduct transactions without revealing their identities or personal information. This privacy makes it attractive for illegal activities such as buying and selling drugs, weapons, and stolen data. Bitcoin, being the most widely used cryptocurrency, is frequently involved in these crimes. The web of anonymity created by Bitcoin and other cryptocurrencies on the dark web has contributed to the rise of various cryptocurrency crimes. Bitcoin’s anonymity and the lack of a centralized authority make it an attractive tool for money launderers. Overall, dark web bitcoin exchanges and wallets provide a means for individuals to engage in anonymous transactions using the cryptocurrency.
Facebook Onion Site
Bitcoin transactions on the dark web have had a significant impact on the price volatility of this digital currency. The anonymous nature of these transactions makes it difficult for authorities to track and regulate them effectively. This lack of oversight can lead to market manipulation and price manipulation. Additionally, the trustworthiness of dark web bitcoin mixers is a concern. Some mixers may be operated with malicious intent, aiming to steal users’ bitcoins or expose their identities. Users risk sending their funds to untrustworthy mixers and never receiving them back.



