Just remember that this is a Dark Web resource, which means that much of the content is likely in breach of copyright. That said, it is one of the most famous and popular Dark Web sites, and it does have legitimate uses. For instance, in the UK, any book older than 70 years old (past the date of the author’s death) is no longer subject to copyright restrictions. This means you can safely download older manuscripts and other public domain works. Torch is the oldest and largest .onion search engine with more than 1 million .onion sites indexed.
- If your personal data ends up for sale on the dark web, it can lead to serious consequences like identity theft, financial fraud, or unauthorized access to your online accounts.
- By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet.
- However, there are plenty of legal and legitimate online activities that require privacy and anonymity.
- For example, it can help users communicate in environments or geographical areas where free speech isn’t protected.
- Civil libertarians wondered whether there was more to the Silk Road shutdowns than the FBI revealed.
Understanding both the potential dangers and the positive uses of Tor and the Darknet is essential for navigating this complex digital landscape. Because of its anonymity, the dark web is filled with illegal services and is used by numerous criminal groups, including ransomware gangs. It is also used by whistle-blowers, journalists, and other individuals who are not involved in illegal activity but need to protect their communications and identities. Through the dark web, users in places of high censorship can also access information and news.
In 2004two years after Tor went onlinethe laboratory made the software available for free to any Internet user. Tor has over two million daily users, with about 13 percent in the US. The US State Department and the National Science Foundation support the Tor Project through grants. Background research tasks included learning from past drug lords, researching legal matters, studying law enforcement agency tactics and obtaining legal representation.
Why Monitor Deep And Dark Web Credit Card Sites?
For certain groups, dark and deep web (DDW) forums exist for anonymous chatting and discussion on sensitive topics like government censorship and more. Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use. Hidden Facebook is hardly the only social media client on the dark web. So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers. There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game. The major issue with these websites is that a whopping 50 percent are fake, and there’s no way of telling for sure if they’ll deliver or not.
How Did We Select These Best onion Sites?
Moreover, the forum offers discussions around account credential dumps, financial crime tools, and various network infiltration strategies. Despite attempts to take it down and constant law enforcement scrutiny, the forum remains strong and the top leak platform, with a persistent role in the landscape of hacker forums and digital pirates. It has a huge and active user base as well as a marketplace that makes trading of hacked credentials and stolen data seamless. Moreover, Exploit dark web forum features a highly organized structure as well as membership policies that make it attractive to most threat actors. The controlled and professional landscape has led many people to view the forum as the most reliable source. Its popularity can be as a result to the ease of use on it, as the forum features a clean and accessible design with enhanced moderation and a wider scope of the leak topics and sources.
Darknet Marketplaces (DNMs) And How They’re Accessed

Some of the reasons why it’s worth monitoring these hack forums include, ability to detect breaches early, gaining threat actor insights, and third-party risk mitigation. If you’re a company, you might want to monitor the dark web to safeguard your reputation and compliance. If you can find your data even before attackers exploit it can help you prevent PR disasters. Security professionals monitor the dark web forums not only for real-time threat updates and signals, but also as a direct contact with how the cybercriminals operate and think. It’s known that the best place to purchase or even exchange various hacking tools is on the dark web discussion boards. In these forums, you can get stuff like malware, hacking tools, and exploits.
Why Are All The Darknet Markets Down
It was created in 1999 as a secure communication platform for people and groups working on liberatory social change. The platform is protected from government interference and malicious attacks to protect the user. In addition, it ensures that no record of communication is stored. Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal.
- Millions of customers’ personal data, including names, addresses, bank account and credit card account information, and many other forms of sensitive data.
- However, engaging in illegal activities on the darknet is against the law and can result in serious criminal charges.
- Bitcoin was initially used to process payments, offering pseudonymity rather than full anonymity.
- This is a rather strange marketplace since it’s quite small and the vendors on the website have been chosen by the owners to sell on the website.
More On How To Stay Safe On The Dark Web
Services like Random Chat connects you with random people using the same service. Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff. By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP. Privacy and anonymity are the dark web’s hallmarks, thanks to a network of servers that hide users’ identities and locations.
Roundup – Best VPNs
This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. For this reason, you must watch out and avoid opening anything that looks suspicious to you. You risk being targeted for attacks if you explore the dark web without protection. The threat can extend to your entire network of devices connected to the internet.
Subscribe To Our Blog For More News And Updates!
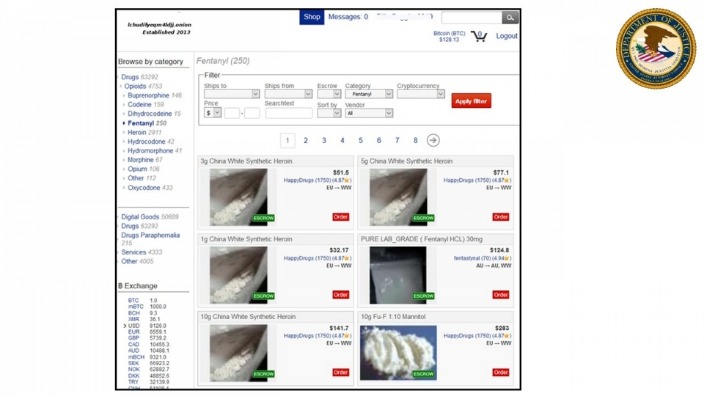
This strategy, along with a strict sign-up process, helped it grow fast. The goal is simple — make financial fraud easy and get as much attention as possible. In addition to counterfeit merchandise, MGM Grand Market offers access to stolen credit card information, compromised bank accounts, and other financial fraud-related services.
Some sites are perfectly legit—such as domain services and email providers. Some—like whistleblowing—may face government censorship in your country. You’ll find black markets selling drugs and other substances, grisly images, and even new identities and online accounts for sale. Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for.
Access The Dark Web Safely
Experienced blogger with a strong focus on technology, currently advancing towards a career in IT Security Analysis. I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world. It serves the same purpose as ProPublica – facilitating access in countries where it may otherwise be restricted.
Despite a 2019 breach that exposed over 26 million credit cards, it continues to operate, indicating sustained trust in its data pipelines. Track and analyze darknet activities using our advanced cyber threat intelligence platform to stay ahead of emerging threats. Fresh Tools Market has become a go-to platform for cybercriminals seeking access to malicious software such as keyloggers, Remote Access Trojans (RATs), and ransomware-as-a-service. The platform is favored by cybercriminals seeking access to accounts that can be exploited for fraud or sold to others.
Like other marketplaces, it also requires registration for new users and accepts payments in Monero. Empire Market is a dark web shop that resembles the AlphaBay marketplace. Its look, design, options, and interface are exactly the exact copy of its competitor, but everything else, including buyers, vendors, and servers, is different. At its launch, the platform accepted payments through Litecoin, but now it has incorporated support for other payment methods like Monero and Bitcoin. The platform also cares about its users and uses PGP encryption and two-factor authentication to secure their data and communication. Its intuitive interface and advanced search features make it easy to find local and global products.
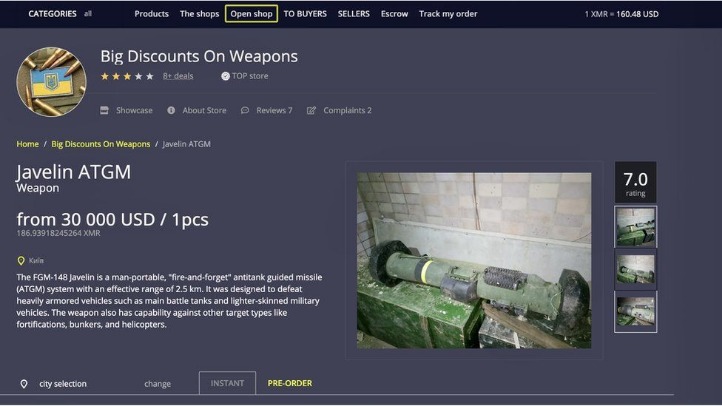
This guide provides verified .onion links, market stats, and expert insights into Tor and Monero usage as of February 21, 2025. The dark web contains content that’s only accessible through networks like Tor. Tor browsers create encrypted entry points and pathways for the user, so dark web activity remains anonymous. The encryption technology routes users’ data through a large number of intermediate servers, which protects the users’ identity and guarantees anonymity. With many dark web marketplaces coming and going, finding a safe and reputable platform is more important than ever. In 2025, only a few markets stand out for their security, reliability, and vendor quality.