
There’s a wealth of information shared among carders—from how to bypass anti-fraud systems to practical guides on using stolen credit cards—all of which helps keep the ecosystem active and evolving. After hackers collect this info, they post it to one of the dark web marketplaces where it can be sold. The leaked data from the BriansClub hack showed that stolen cards from U.S. residents made criminals about $13 to $17 each, while those outside the U.S. sold for up to $35.70, Krebs reported. When hundreds or thousands are bought at once, that becomes a lucrative crime. “The dumps also include magnetic stripe data, allowing criminals to create physical card clones,” Draghetti warned.
Where To Find Darknet Market Links Redit
While this is convenient, it places your credit card information at risk of being exposed in public data breaches, so it’s best to never save it on websites. They are used by mid-level and highly experienced fraudsters who know how to use them effectively. Gathering resources is usually the first phase for criminals who want to commit fraud. Obtaining good quality materials is always an important part to being a successful craftsman – it is no different for those involved in carding fraud. As Figure 2 demonstrates, one of the largest dark web marketplaces, Alphabay, runs its own credit card shop as an additional feature of the site. Skilled hackers can take the stolen credit card number and replicate it onto a blank card using specialized equipment.
Secure Devices
UniCC has filled the void left in the underground carding market after Joker’s Stash, deemed one of the founders of the carding industry in the dark web, voluntarily pulled the plug in February 2021. It’s believed that the administrator behind Joker’s Stash came away a “Bitcoin billionaire”. And so, after nearly a decade of being active, administrators have announced their “retirement” on a carding forum. The operators of BidenCash have caused significant harm to millions of victims whose personal and financial information has been compromised. This material may not be published, broadcast, rewritten, or redistributed.
How To Use Tools To Detect And Flare Up Potential Fraud
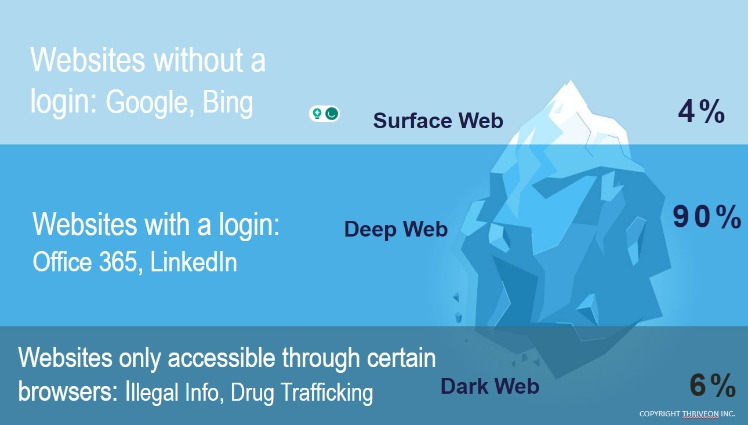
These are websites such as newspapers, blogs, Wikipedia, etc., that can be accessed through traditional search engines and don’t require any special efforts or credentials to access. Of the Italian cards, roughly 50% have already been blocked due to the issuing banks having detected fraudulent activity, which means that the actually usable entries in the leaked collection may be as low as 10%. BidenCash is a stolen cards marketplace launched in June 2022, leaking a few thousand cards as a promotional move. To pull off these credit card scams, D2 and other fraudsters would sign onto sites on the dark web and simply pay a small fee—as little as $35 — for victims’ credit card information. Credit cards, Paypal accounts, and fullz are the most popular types of stolen information traded on the dark web, but they’re far from the only data worth stealing. Sales of passports, driver’s licenses, frequent flyer miles, streaming accounts, dating profiles, social media accounts, bank accounts, and debit cards are also common, but not nearly as popular.
On the contrary, the dark web is also used for legitimate purposes, with journalists, whistleblowers, and social or human rights activists often using it to communicate securely. From the data D3Labs has examined so far, about 30% appear to be fresh, so if this applies roughly to the entire dump, at least 350,000 cards would still be valid. To ensure larger reach, the crooks distribute the collection via a clearnet domain and on other hacking and carding forums. Get the latest updates on privacy, plus expert tips, and security guides to up your digital protection game. Some fullz even include photos or scans of identification cards, such as a passport or driver’s license. While SSN, name, and DOB are all fairly standard in fullz, other information can be included or excluded and thereby change the price.

New Report On James Comey Suggests ‘ongoing Conspiracy’ Against Republicans, John Solomon Argues
Then to round off the year, ToRReZ Market, a site selling illegal products, closed in December 2021. UniCC and Joker’s Stash aren’t the only carding markets that have voluntarily exited this illicit industry. See my tips and best picks on how to protect yourself from identity theft by searching “identity theft” at CyberGuy.com by clicking the magnifying glass icon at the top of my website.
- With this stolen information, fraudsters can make unauthorized purchases, withdraw funds, or even create counterfeit credit cards.
- We believe everyone should be able to make financial decisions with confidence.
- Threat actors insert malicious code either into the third-party payment processors or directly into the websites that copy all the information entered on a form.
- When one goes down, two more emerge with new ideas, better technology, and greater difficulty to track.
Covid-19 Vaccines Being Sold On Darknet
Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data. Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading. Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet. Established in 2022, Torzon market is one of the biggest and most diverse marketplaces on the dark web.
Easily initiate data encryption on your external drives and disks, ensuring compliance with your specific company policies. Encryption-2-Go offers controlled encryption, container-based or directory encryption, and even detects existing BitLocker To Go encrypted drives. With configurable user selection dialogs, it provides a user-friendly experience while maintaining strict security. As you discover the hidden depths of the web, ensure your sensitive data remains protected, no matter where it travels. The ease with which any item, from stolen physical things such as credit cards to huge dumps of personal information, can be found and bought online should give everyone pause.
The Rise Of Credit Card Fraud
Russian Market has consistently remained one of the most popular and valuable data stores on the dark web. The platform’s activity has increased significantly over the past year, indicating its growing influence and market share in the underground economy. While this topic may seem distant for most people, understanding how these spaces operate is crucial. It helps us stay more vigilant, better protect ourselves, and make informed decisions online. Experts suggest that this giveaway serves as a marketing ploy to attract new users to B1ack’s Stash and establish its dominance in the competitive carding market.
Thieves often buy cards to use on specific sites that don’t have security features like Verified by Visa (VBV) or MasterCard’s SecureCode. According to research conducted by the BBC, Europol, and European Monitoring Centre for Drugs and Drug Addiction (EMCDDA), there are at least five known reasons why markets in the dark web close. The Internet is a vast and complex landscape, much larger than the familiar interface we use every day. David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego. These are often compiled from multiple sources — often from multiple breaches and other similar databases; these rarely cost more than US$100 and can contain millions of records.
The data dump disaster includes some complete names, expiration dates, CCV and unique email addresses. From drug trafficking to arms deals to stolen data, the dark web provides a marketplace for many illegal goods and services. This has led to a negative reputation and is attracting the attention of law enforcement agencies.
Next, let’s explore how individuals can access the Dark Web safely, while minimizing personal risks and vulnerabilities. Experience Flare for yourself and see why Flare is used by organization’s including federal law enforcement, Fortune 50, financial institutions, and software startups. The intelligence gathered from these markets helps security teams predict and prevent future attacks. By monitoring the dark web, you can quickly identify when your cards are compromised through partner organizations or merchants. Network segmentation is absolutely critical for businesses handling card data. One particularly interesting detection method involves monitoring dark web markets themselves.

By understanding what these sites are, their functions, and how to protect oneself, individuals can navigate the complexities of the dark web with greater awareness. Exploring the realm of credit card transactions on the Dark Web is a journey into a dangerous and illegal world. While the allure of cheap credit card details and the potential for financial gain may be tempting, the risks and consequences of engaging in such activities cannot be ignored. Stolen credit card details are sold for a fraction of their actual value, making it an attractive option for fraudsters looking to finance their criminal activities.

Also, you must alert the credit-reporting firms — Equifax, Experian and TransUnion are the biggest — to freeze your report at each of them. The answer lies behind distributed denial of service (DDoS) attacks that targeted its original domains. As a result, in order for word to get out in regard to fresh URLs for the service, the hackers are distributing the data free of charge. Install reputable antivirus software to detect and prevent malware infections. As mobile payments become more popular, carders have shifted their focus to exploiting vulnerabilities in mobile payment systems. Paul C Dwyer, President of the International Cyber Threat Task Force, examines the regulatory and operational questions raised by the cyberattack on M&S.
With just a few taps, people can see exactly where their money goes and catch problems early. Such type of data is likely to have been compromised online, making it a red flag for would-be fraudsters. Group-IB’s cybercrime research unit has detected two major leaks of cards relating to Indian banks in the past several months.



