
Once you upload something, it stays there indefinitely even if you stop using Freenet, so long as it is popular. Tor over VPN requires you to place some trust in your VPN provider but not your ISP, and is best if you want to access .onion websites. VPN over Tor requires you to place trust in your ISP but not your VPN and is best if you want to avoid bad Tor exit nodes. Some consider VPN over Tor more secure because it maintains anonymity throughout the entire process (assuming you pay for your VPN anonymously). Although the official Tor Project advises against VPN over Tor, both methods are superior to not using a VPN at all. Tor over VPN also doesn’t protect users from malicious Tor exit nodes.
That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web. Then, you can set up 2FA (two-factor authentication) for that extra touch of security in case someone somehow figures out your password. If you ever have to connect to public Wi-Fi, make sure to use a VPN to keep your browsing safe and private. According to a recent trend, the dark marketplaces faced a decline in revenue. Chainanalysis, a blockchain analysis firm, conducted research that shows that the revenue decreased from $3.1 billion (2021) to $2 billion (2024).

VendorLink
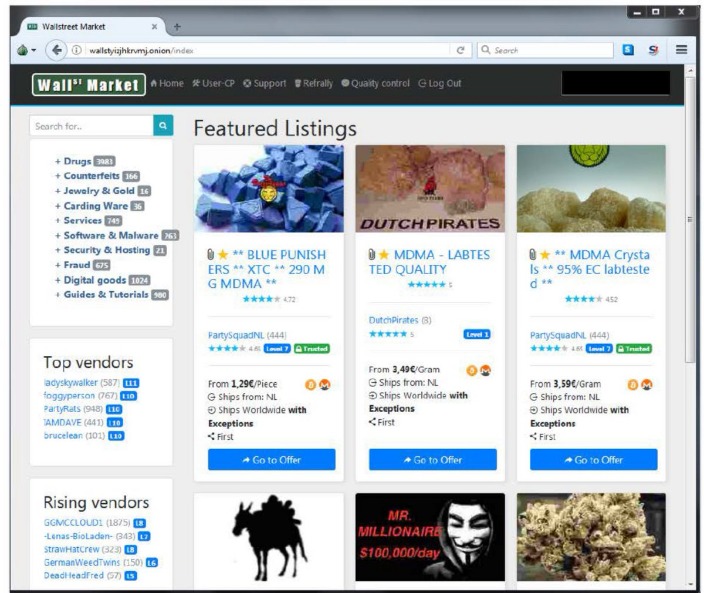
The market facilitates trades in stolen credit card data, hacked bank accounts, and services to facilitate the laundering of cryptocurrency. With Tor installed, you’ll next need to find a darknet marketplace domain to visit. The Tor network mandates that Tor clients (such as the Tor browser) can only access sites using the .onion TLD. However, these domains are not easy to distinguish, and are usually represented in long, often randomly generated alpha-numeric strings. Finding the correctly represented URL for a particular domain in the first instance can be a challenge.
The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight. These features help establish trust between buyers and sellers, providing users with a sense of security that many other markets lack. Bazaar marketplace is known for a wide range of products (drugs, fraud tools) and a straightforward interface. It enforces multisig escrow on all transactions and has an active customer support Breaking Bad Forum.
Verified Social Channels And News Sites

Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook. This .onion link makes it impossible for hackers to impersonate your profile. Formerly known as Archive.is, it is one of the best onion sites on the dark web. It aims to preserve the internet’s scientific and cultural heritage.
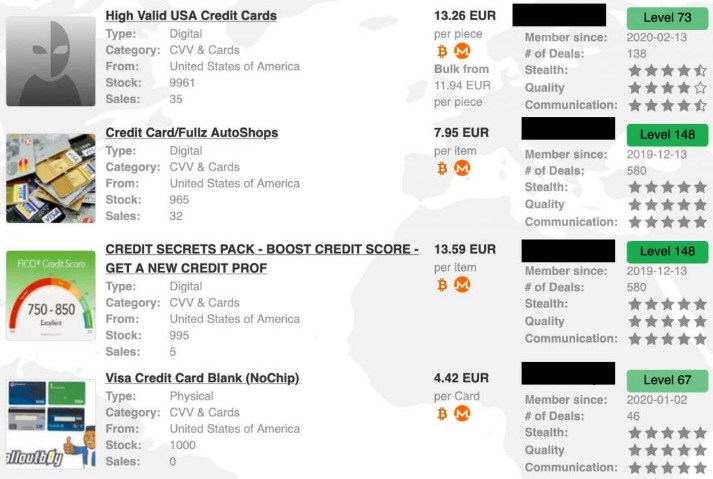
How Much Is Stolen Data Sold For On Darknet Markets?
It’s important to only visit trusted sites and avoid clicking on suspicious links. However, you can trace its roots to the development of technologies like the Tor network or Freenet. In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet. This was the initial framework for anonymous communication and file sharing. It scans darknet marketplaces and hacker forums to alert you instantly if anything shows up. This way, you can catch any leaks and stop them before they cause bigger problems.

Darknet Markets Explained: Navigating The Hidden Web
At checkout, you will be asked to provide your shipping address and payment information. Most darknet markets accept Bitcoin as payment, so you will need to have a Bitcoin wallet set up before making a purchase. Some markets may also accept other cryptocurrencies, such as Monero or Ethereum. Now, some kids try something bad and they get caught, and they get in trouble, and they decide not to do that again.
Online Drug Sales Triple After Silk Road Closure, Says Report (nbcnewscom)
The site gives out free samples of the stolen data every now and then to gain more customers. With its fast rise to fame and focus on money fraud, it’s no surprise that cybersecurity experts are keeping a very close eye on this one. Want to get illegal drugs, fake passports, Trojan, or other cyber attack software? Understandably, as in the case with most illicit trade markets, you don’t even need to verify your email Awazon. Jacob Riggs is a senior cyber security professional based in the UK with over a decade of experience working to improve the cyber security of various private, public, and third sector organisations.
This one became popular during the pandemic as everyone shifted to remote work, but the issue persists. Cyber criminals are posting and selling verified Zoom accounts on the dark web. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails.
See Why DarkOwl Is The Leader In Darknet Data
So don’t be surprised if you encounter different versions that claim to be genuine, and be very careful. We deliver contextualized, actionable intelligence through our dedicated platform or API integration, ensuring that you can respond effectively to darknet threats. With over 20 years of experience in cybersecurity and marketing, Ben has held leadership roles at companies like Check Point, Cognyte, Cylus, and Ionix.
- Even if you’ve never visited these markets, your personal and financial data might already be there, having been leaked through a data breach.
- Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide.
- Open up Tor, and you won’t suddenly see the dark web staring back at you.
- The website allows a personalized searching experience, where you can search according to your geographical location, country-specific, and keyword or price-specific search results.
- Its intuitive interface and advanced search features make it easy to find local and global products.
- Absolutely no one knows who’s surfing on the dark web, who is selling, who is buying or anything like that – as long as you take the correct safety and online privacy precautions.
A Quick Guide On How To Use A VPN With Tor
The easiest way to access Tor is through a special browser known as the Tor Browser. You might want to hide your Tor Browser download using a VPN and your existing browser’s private/incognito mode. Our rigorous research and testing have revealed revealing truths and busted myths. We’ll navigate this intricate maze with you, uncovering its secrets while ensuring your online safety. For several years, Yahoo was at the apex as the internet’s best web service provider, offering…
- As it’s inaccessible via the surface web, users require a software known as The Onion Router (or TOR) to get to the darknet.
- It allows you to buy and sell a wide range of products and services with a good user experience.
- And, while many people would be alarmed at the prospect of their teenagers buying drugs online, Silk Road was a whole lot more professional, regulated and controlled than buying drugs offline.
- Tor markets, also known as darknet markets, are online marketplaces that operate on the Tor network, allowing users to buy and sell goods and services anonymously.
What Kind Of Content Is On The Dark Web?
Although eight of the darknet markets active in 2018 closed in 2019, eight new ones opened, keeping the total number of active markets steady at 49. On average, each active market in 2019 collected more revenue than those active in any other year, apart from during the height of Silk Road’s heyday in 2012 and 2013. Once you’ve chosen a marketplace, you’ll need to create an account. This will usually involve providing an email address and choosing a username and password. Be sure to use a strong password and avoid using any personal information in your username or email address.
Afterwards, your request will be matched with the appropriate website. Tricky, but effective; that’s why it’s, by far, the best method to access dark web content. Unlike regular browsers that directly connect to websites via your ISP’s DNS, Tor anonymizes your journey by routing your request through several relays before reaching its destination. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web. For recommendations on choosing a VPN, look for expert reviews and articles.
Darknet marketplaces like to exist on the dark web because it offers a service that the regular internet, or more accurately, the “surface web,” does not. Although these marketplaces are continuously shut down by law enforcement agencies, they still work today. Interestingly, new sites get more hype, and it even becomes difficult to shut them down, as they have better security than the older ones. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. It’s easy to fall prey to unscrupulous vendors, fake marketplaces or phishing attempts.



