Launched in 2020, Cypher Marketplace sells fraudulent documents, stolen credit cards, fake IDs, and malware. Its emphasis on user anonymity and document forgery makes it a core tool for identity fraud. Founded in 2014, BriansClub remains one of the oldest and most infamous dark web markets for stolen credit cards, fullz (complete identity kits), and dumps. Insider trading on the dark web may seem like an easy way to gain an edge in the stock market, but it is a highly illegal and risky practice that can result in severe legal and financial consequences. To protect themselves from scams and legal troubles, investors should rely on legitimate sources of insider information and follow SEC regulations and guidelines when researching a company.
Ready To Explore Web Data At Scale?
It hosted over 7,000 .onion categorized links to make surfing the web easier. One of Daniel’s impressive features was the built-in functionality that showed whether a particular dark website is online. After more than a year of no updates, the site admin shut it down, reasoning that he couldn’t keep the list of onion links up-to-date. A budget-friendly VPN service allowing users to access dark web safely anytime, anywhere, and on any number of devices they want. This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session.

Accessing Onion Sites On Android
Patterns recommended to avoid include hiring hitmen like Dread Pirate Roberts, and sharing handles for software questions on sites like Stack Exchange. BidenCash became known for regularly leaking huge amounts of stolen credit card data and personal information — often for free. This strategy, along with a strict sign-up process, helped it grow fast.
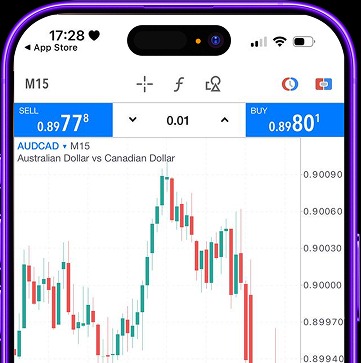
Furthermore, conducting a cybersecurity gap analysis ensures that SMEs can identify weaknesses and take targeted action to mitigate risks. Insider trading is illegal and can have serious consequences if you are caught. It is important to be aware of the laws and regulations in your jurisdiction. For example, in the US, the SEC has strict rules about insider trading and it is important to understand those rules before engaging in any trading activity. One of the main rewards of insider trading on the dark web is access to non-public information.

We find that half of the DWM users trade through U2U pairs generating a total trading volume greater than DWMs themselves. We then show that hundreds of thousands of DWM users form stable trading pairs that are persistent over time. Users in such stable pairs turn out to be the ones with the largest trading volume on DWMs. Then, we show that new U2U pairs often form while both users are active on the same DWM, suggesting the marketplace may serve as a catalyst for new direct trading relationships.
Buying Stocks Using Non-public Information?
Under these conditions, uninformed traders gravitate towards the dark pool because they face lower risk of adverse selection there. In European markets, the volume of trading executed in dark pools accounted for 9.1% and 9.6% of all on-exchange activity in April and July 2019, respectively. The proliferation of dark pools has been driven in part by a greater reliance on technology for trading in financial markets.
Drughub Market
Full identity kits — including SSNs, addresses, and banking details — fetch higher prices. Another way that insider trading occurs on the dark web is through the use of hacked information. Hackers can gain access to confidential information about companies and then sell it to traders on the dark web. This information can include trade secrets, customer data, and other valuable information that can give traders an edge in the market. The structural change in the multiseller network and the resilience of the multibuyer network. Temporal network of multisellers (top) and multibuyers (bottom) between markets for each year.
Market Value And Popularity
As a result, you should avoid opening unfiltered sources, torrent sites, and dark web links unnecessarily and downloading every file you come across. For this reason, you must watch out and avoid opening anything that looks suspicious to you. Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally.
C Notable Cases That Illustrate The Impact Of Insider Trading On The Dark Web
Future work may further extend the approach presented here, for example using machine learning methods to capture further behavioral regularities. Third, at any given moment we classify entities as either buyers or sellers. For example, in some cases, a seller in a given market may behave as a buyer in a second market or in the U2U network.
Government Monitoring
- Until the end of 2013, when Silk Road is the dominant market (see Fig. 3), market-only sellers is the dominant category, and there are no multisellers.
- A top-of-the-line VPN network that ensures maximum security while accessing dark sites online.
- Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble.
- Built with a focus on privacy, it supports transactions in Bitcoin and Monero, ensuring untraceable purchases.
- You can see all the product categories the marketplace deals with on the homepage.
- First, we propose a simple algorithm to identify buyers and sellers.
Some scholars believe that the rise of virtual currencies such as Bitcoin has exactly solved this problem. The dark web, also known as the hidden web, is a hidden server contained in the “deep web”. As opposed to the surface web, it exists on the World Wide Web in the hidden web.
Insider Trading On The Dark Web
It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. The Tor browser gives employees a marketplace to exchange insider information on their firms for Bitcoin or insider information on other public firms.
These listings often include detailed descriptions, user reviews, and even shipping guarantees. And beware—while many explore out of curiosity or for research purposes, it’s important to remember that engaging with these platforms, even as an observer, can lead to serious legal and ethical consequences. Since Bitcoin has no issuing agency, there is no crisis of being frozen like ordinary currencies, and it has become a new way for criminals to blackmail. In May 2017, the Wanna Cry ransomware became popular all over the world. Virus makers locked “poisoned” users and demanded payment of a certain amount of Bitcoin as the price of unlocking. Manual monitoring of the dark web is inefficient and risky due to the sheer volume of data involved.
In the first arc of the anime series Lupin the 3rd Part V, Lupin III steals digital currency from the “Marco Polo” darknet market. He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests. More recently, in September 2024, the BKA and ZIT announced the dismantling of dozens of cryptocurrency exchanges that they accused of enabling money laundering and other offenses.



