
Over 400 millionusers are protected by Kaspersky technologies and we help over 220,000corporate clients protect what matters most to them. In recent years, darknet markets have become increasingly popular, with new marketplaces popping up all the time. According to a report by the European Monitoring Centre for Drugs and Drug Addiction, there were more than 50 active darknet markets in 2021, with a total of over 300,000 listings. This is a significant increase from just a few years ago, when there were only a handful of active markets. Market lists, often updated regularly, provide users with direct access to active onion URLs, reducing the risk of phishing or scams.

What Kind Of Content Is On The Dark Web?
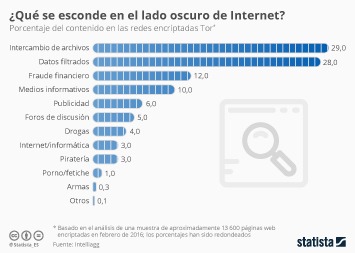
Level 1 vendors can supposedly have their information removed by paying a $100 fee. However, larger “Level 5” vendors are asked to cough up $20,000 payments. If you’re going to access these markets regardless of warnings, you deserve accurate information about security practices and risk mitigation. This article reveals the top 10 dark web markets dominating in 2025, their unique characteristics, and the critical implications for enterprise cybersecurity.
What Is The Most Popular Darknet Marketplace In 2025?
The darknet has been a hot topic in recent years, with many people wondering what it is and how it works. In simple terms, the darknet is a part of the internet that is not indexed by search engines, making it difficult to access without specialized software. One of the most popular uses of the darknet is for online marketplaces, also known as darknet markets or DNMs. In recent years, some darknet markets and fraud shops have been integrating crypto payment processors on their websites via APIs, possibly as a way to improve operational efficiency and increase security.
Using his credentials, cybercriminals committed a variety of online fraud activity over the course of six months. In 2019, the FBI started its investigation into Genesis Market and enlisted other government agencies and law enforcement organizations across the world, working towards the market’s closure on April 4, 2023. As part of the investigation, the Dutch National Police took the lead on cybercrime prevention, and Van Well shared his insight on the sophistication of the fraud shop’s operation.
These sites often look basic or outdated, and their URLs are lengthy strings of random letters and numbers. Keep in mind that visiting the dark web isn’t illegal, but engaging in criminal activity there is. To turn it on, just go to the “Settings” and then the “Tools” section of the NordVPN app and activate “Dark Web Monitoring.” In the end, it’s all about staying one step ahead. The more proactive you are, the better you can protect yourself against identity theft and other cyber threats.
Kaspersky Uncovers Efimer Trojan Targeting Organizations Through Phishing Emails
Every single market listed here goes through our verification gauntlet – and honestly, most don’t make it through. Since 2020, 2easy has sold massive stealer logs with sensitive data like passwords, bank cards, and initial access credentials. It supports operations in multiple languages and operates on both clearnet and Tor.
Why Is Tor So Slow?
Fraud-related products, consumer electronicselectronics, self-defense products, and even hosting. In addition to its emphasis on stolen credentials, 2easy Market offers a variety of cybercrime tools, such as hacking services, exploit kits, and other resources for conducting cyberattacks. Unlike many other dark web markets, Cypher does not require buyers to deposit cryptocurrency upfront, which reduces the risk of exit scams. This marketplace focuses on selling stolen financial data, such as BINs (Bank Identification Numbers), RDP/VDS access, and verified crypto accounts for money laundering. These features help establish trust between buyers and sellers, providing users with a sense of security that many other markets lack.
Darknet Market Tor Links For 2025 :
Immediately change your passwords, enable two-factor authentication, and notify your bank or credit card provider if the leaked information includes your financial data. You should also consider freezing your credit to prevent identity theft. From there, these products are then passed on to distributors, which are the dark web marketplaces in this context.
- We hypothesize that the true damage of scamming is greater than what reporting to the FBI and our on-chain metrics show, but overall, scamming is down, given broader market dynamics.
- The website allows visitors to view all the goods and services on display before they buy something.
- However, larger “Level 5” vendors are asked to cough up $20,000 payments.
- Of course, it is impossible to cover every type of the websites published in the dark web.
- The future appears to be focused on enhanced security, broader offerings, and a continued cat-and-mouse game with law enforcement.
Darknet Communications In 2025 – From IRC Forums To Telegram Crime Networks
Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content. The markets often share materials related to child exploitation, pornography, and non-consensual recordings, all of which are serious crimes that inflict lasting harm on real-life victims. Such content fuels a dangerous cycle of abuse, violence, and exploitation. Purchases through links on our pages may yield affiliate revenue for us.
- We review and list tools and products without bias, regardless of potential commissions.
- Given the size and impact of the FTX situation, we are treating it as an exception to our usual on-chain methodology.
- Haystak also offers a premium version that allows advanced search, access to historical content, and email alerts.
- Exclusive Monero usage signals a heightened prioritisation of anonymity.
- With stricter Know Your Customer (KYC) and Anti-Money Laundering (AML) measures, illicit actors are facing greater challenges when attempting to cash out.
- High-rated vendors often gain more visibility, which incentivizes others to maintain high standards.
That’s why we recommend connecting to VPN before accessing Tor—VPN encryption protects your data, and changing your IP adds an extra layer of privacy to protect you. The three nodes separate your IP address from your destination and enable two individuals to communicate without either party, or any middleman, knowing who the other is. Needless to say, it takes your data much longer to travel this way, which means dark web links load slowly compared to indexed sites. Onion sites (aka Tor sites) are websites only accessible on the dark web; you can’t view them using a regular browser. Their URLs (aka dark web links) have .onion as the domain, instead of the common surface web domains like .com or .net. The landscape of darkweb markets is dynamic, influenced by technological, economic, and regulatory factors.
From stolen credit card information to hacking tools, the darknet market has become a one-stop-shop for cybercriminals. Darknet or dark web marketplaces are a hidden part of the internet that surface web users can’t access; they can only be accessed with special anonymity software called Tor. Many people (mostly criminals) use these sites to perform illegal transactions such as selling banned goods and services. We report on certain defined categories — stolen funds, darknet markets, and ransomware, to name a few — on an annual basis. In particular, we have seen the emergence of large-scale on-chain services that provide infrastructure for numerous types of illicit actors to help them launder their ill-gotten crypto. The evolution of darknet markets in 2025 has significantly enhanced the security and reliability of drug trade, making them a preferred platform for users seeking anonymity and quality.
Industries That Benefit The Most From Dark Web Monitoring 2025
It works kind of like a VPN, but instead of routing your traffic through one remote server, it routes it through many random servers across the globe. Counterfeit goods are products that are made to imitate genuine items with the intention of deceiving others. They can be used for financial crime, identify theft, as well as counterfeit goods.
1 Transaction volume is a measure of all economic activity, a proxy for funds changing hands. We remove peel chains, internal service transactions, change, and any other type of transaction that would not count as an economic transaction between distinct economic actors. Similarly, this year’s growth in darknet market revenue also comes after a 2022 decline in revenue. That decline was driven largely by the shutdown of Hydra, which was once the world’s most dominant market by far, capturing over 90% of all darknet market revenue at its peak. While no single market has yet emerged to take its place, the sector as a whole is rebounding, with total revenue climbing back towards its 2021 highs. Crypto hacking, on the other hand, is much more difficult for criminals to hide, as industry observers can quickly spot the unusual outflows from a given service or protocol when a hack occurs.



