
Bitcoin’s blockchain is too leaky these days, and markets like Archetyp going Monero-only prove it. Mixers help, sure, but XMR’s built-in privacy is why I’ve switched my stash over. Jumping into the dark web can feel like a maze, but it’s pretty doable once you’ve got the basics down. First off, you’ll need the Tor Browser—think of it as your ticket in. It’s free, masks your IP, and bounces your connection around so no one’s peeking over your shoulder. I grabbed mine from the official site a while back after dodging a sketchy mirror that tried to sneak in some junk software.
To access the marketplace, dark web users must register first and pass the CAPTCHA test to prove they are human. Some believe STYX is the OG darknet market when it comes to financial crimes. It trades in hacked bank accounts, stolen credit card information, and other services that facilitate cryptocurrency laundering. The market started in 2021 in Canada and features both international and Canadian users.

Is Claude Safe And Secure In 2025?
Unfortunately, it requires you to have an invitation code to create an account. This means you have to know someone who is already using the platform. Even without the code, you can visit the security section to get tips on improving your daily life privacy. This service is a good source of statistics if you have a school project requiring research on Tor and the dark web. However, note that the site only uses non-sensitive and public data for the metrics. The Tor Metrics is a good place to get more information about the Tor project.
Secure Your Tor Setup
It’s known for its strong security features (like a trusted escrow system, PGP two-factor authentication) and anonymity. While this market started in Canada in 2021, WeTheNorth now sells to both Canadian and international users. It’s a market for fake documents, hacking software, and financial fraud services. WeTheNorth has a strong community vibe, with an active forum where users interact and share updates.
Shifts In User Behavior And Marketplace Structures
- How Kaspersky researchers obtained all stages of the Operation Triangulation campaign targeting iPhones and iPads, including zero-day exploits, validators, TriangleDB implant and additional modules.
- That’s exactly what happens when it comes to the dark web marketplaces.
- By continuing further, you acknowledge that you will not use any links, graphic, or anything else on this article for any illegal activity, including buying/selling of drugs.
- They seized control of the market’s servers and continued operating it covertly for weeks, gathering extensive intelligence on vendors, buyers, and operational networks before shutting it down permanently.
- The Genesis Marketplace also has a full featured help desk with a ticketing system.
Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed. Besides, victims of crime may want to hide their identities from their perpetrators. Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble.
FreshTools, founded in 2019, specializes in selling stolen account credentials and data, particularly webmail, RDPs (Remote Desktop Protocols), and cPanels. Founded in 2020, Cypher Market has carved out a niche on the dark web by focusing on cybercrime products. Bohemia entered the dark web scene in May 2021, quickly rising due to its modern interface and strict rules that reduce the likelihood of scams. There are plenty of safety precautions as well to help protect customers.

Tor Stuff
These sites operate as self-contained platforms with .onion addresses that are not indexed by Google. Users need the Tor Browser to resolve these URLs (Tor routes traffic through multiple encrypted relays to hide your IP). Security is the backbone of darknet markets, ensuring trust and anonymity in an ecosystem where traditional safeguards don’t apply. This section explores the security practices of our top 10 darknet rankings as of February 27, 2025, detailing how these platforms protect users, vendors, and transactions within their onion marketplaces. From encryption protocols and two-factor authentication (2FA) to escrow systems, DDoS protection, and uptime strategies, these practices define the reliability of crypto trading platforms and dark pool trading hubs.
However, theories provide perspectives as to why counterfeiting occurs and how it might be addressed. Capable guardians can include those involved in security at country borders or those involved in inspecting goods at other stages of the supply chain (Marucheck et al., 2011; Tang, 2006). For example, when manufactured products are transported, transport personnel and employees could also act as guardians (Hollis & Wilson, 2014).
Run Antivirus/Anti-Malware Software
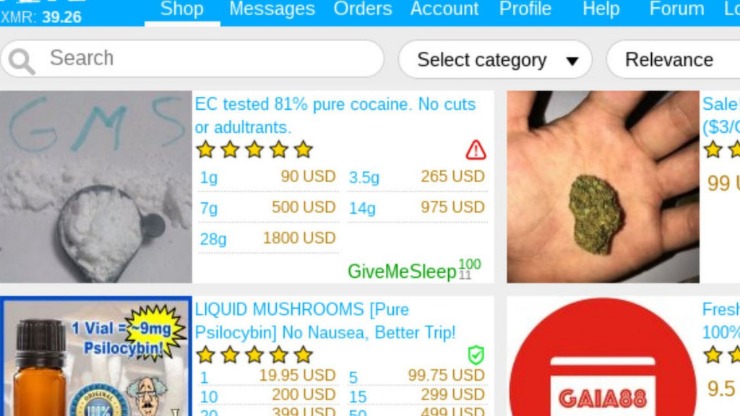
You’ll find reviews, quick tables with the nitty-gritty details, and some practical tips on using Monero (see how) or setting up PGP (check it out). Plus, we’ve got some fresh takes on dark web trends and how to get started. By leveraging automated dark web monitoring, organizations can mitigate risks, and take preventive measures before the leaked data is exploited. In addition to its emphasis on stolen credentials, 2easy Market offers a variety of cybercrime tools, such as hacking services, exploit kits, and other resources for conducting cyberattacks. This platform has rapidly become a key player in the fraud market, trading in PII and SSH credentials while making use of both the clear and dark web.
Darknet Markets Explained: Navigating The Hidden Web
Although the underground internet world is rife with everything bad, it also hosts positive elements. The weighted mean is the result of taking the sum of the product of the category price and the number of listings of the same category, divided by the total number of listings. Thus, each mean is weighted by the number of listings available in each product category. To better understand the classifier’s performance for each category, we generated a normalized confusion matrix for all classes (Fig. 1). The matrix shows the cases of true (rows) and predicted (columns) categories of the listings. Thus, the values in the matrix show the proportion of items for which the true class was predicted.
They engage in financial crime and sell other people’s stolen personal information, since they’re under the veil of anonymity. But somewhere between production and purchasing, things can get dirty. For example, an insider or factory employee might quietly slip away with an unmarked gun and sell it online. Once it lands on a darknet marketplace, it becomes part of the illegal weapons trade.
Always use a fake name and a temporary email address when you buy something from the dark net shops. You can even use a secure email provider or a burner email address whenever you visit the dark web. Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details. Therefore, for security reasons, disable JavaScript on the Tor browser and enjoy an anonymous browsing experience on the dark net. In April 2016, its APIs were compromised, resulting in stolen messages.
The victims, who are common users, businesses, and even banks, who end up paying the price. It became the blueprint for other dark web marketplaces that tried to take its place. BidenCash was launched in 2022, and since it became a hot spot for cybercriminals to sell and buy illegal things, including stolen card information and personal data. However, in June 2025, BidenCash’s relevant domains (around 145) were seized by the US Department of Justice. Want to get illegal drugs, fake passports, Trojan, or other cyber attack software? Plus, there’s a thorough vetting process for new buyers and sellers to keep the community more secure.
Similarly, cosmetics seem to originate from Austria more frequently, and pharmaceuticals from Australia. Alternatively, counterfeits from the US might be more heavily purchased domestically, leading to limited exportation, which would avoid border controls. Moreover, dark market listings represent the availability of a product rather than the actual supply of them. Although knowing which country counterfeits are available is helpful, products must be purchased first and subsequently shipped to be found at a border. Thus, estimation of product origins from dark markets and measures of seized goods might also vary because they capture products at different supply chain stages. Cybersecurity companies and researchers monitoring darknet markets face legal and ethical restrictions.
Cybercrime units routinely monitor dark web forums, chat platforms, and encrypted messaging services, collecting intelligence and building digital dossiers on high-value targets. Authorities employ advanced data-mining software, network analytics, and artificial intelligence-driven algorithms to detect patterns indicative of illegal trade or fraudulent document production. Given the anonymity and encryption inherent to the dark web, authorities have adapted by developing specialized investigative methods and cross-border cooperation. Listings for fake documents typically detail the quality of the forgery, the region or jurisdiction covered, price ranges, and turnaround times. Vendors often showcase sample images and customer reviews, reinforcing credibility and trust.



