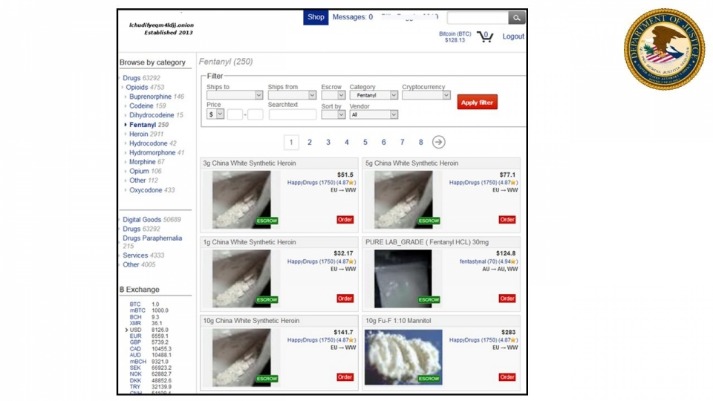
The website has a great design and a clean and organized interface that is easy to use. The homepage includes options like browsing products, searching, mixer, and coin exchange. You need to register first to purchase products from this marketplace. The browser uses onion routing technology to route the internet traffic through multiple relay nodes that provide layered encryption. The layers of encryption hide your data and activity from snooping eyes. You could try to visit a major site like Facebook’s onion site to check if your browser is working at all.
Paying With Monero: A Quick Rundown

Confidential government files and pages tied to unlawful trafficking often get filtered out. While many dark websites appear sketchy, The New York Times is an exception. It offers reliable news coverage without exposing readers to harmful or illegal material. His articles have appeared in many respected technology publications.
What Are Dark Web Websites?
It contains a good selection of product listings that range over 35,000 items. The website has an interface and design similar to other dark web shops. It uses PGP encryption, two-factor authentication, and OPTP authentication to ensure users’ security. Mega Market is a new yet popular shop on the dark web that reached a skyrocketing reputation after the closure of the Hydra market. It allows you to buy and sell a wide range of products and services with a good user experience.

Can You Access The Dark Web With A VPN?
The threat can extend to your entire network of devices connected to the internet. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user. In some countries, evading government restrictions to seek new political ideologies is punishable. For example, China uses the Great Firewall to block access to Western sites. Accessing blocked content can result in being placed on a watch list or imprisonment.
I Legal And Ethical Considerations
This adds extra protection since opening Tor itself encrypts your traffic. A virtual private network (VPN) is a good way to mask Tor activities. It adds an extra encryption layer and passes your traffic through a secondary server of your choice, preventing anyone from seeing that you are accessing the web via Tor. Immediately close your entire Tor Browser window (not just that active tab). Note that engaging with the content in any way is not only distressing but could also put you at legal risk.
- For several years, Yahoo was at the apex as the internet’s best web service provider, offering…
- Right now, you can use many cryptocurrency .onion sites to buy or sell all types of cryptocurrencies.
- You risk being targeted for attacks if you explore the dark web without protection.
- In addition to counterfeit merchandise, MGM Grand Market offers access to stolen credit card information, compromised bank accounts, and other financial fraud-related services.
Encrypted Communication Tools
You can simply visit given onion like to know more about Rapture. To find .onion links for dark web sites, you’ll need to use a dark web search engine. Many of them are safe for beginners to use since they filter out dangerous/illegal content to only provide safe .onion links. My favorites are DuckDuckGo (usually the Tor browser’s default search engine), The Hidden Wiki, and Ahmia. Using a reliable VPN with Tor provides a way to improve security when accessing dark web links. The VPN encrypts your traffic before it enters the Tor network, preventing your ISP from seeing that you’re using Tor.
Trusted Directories
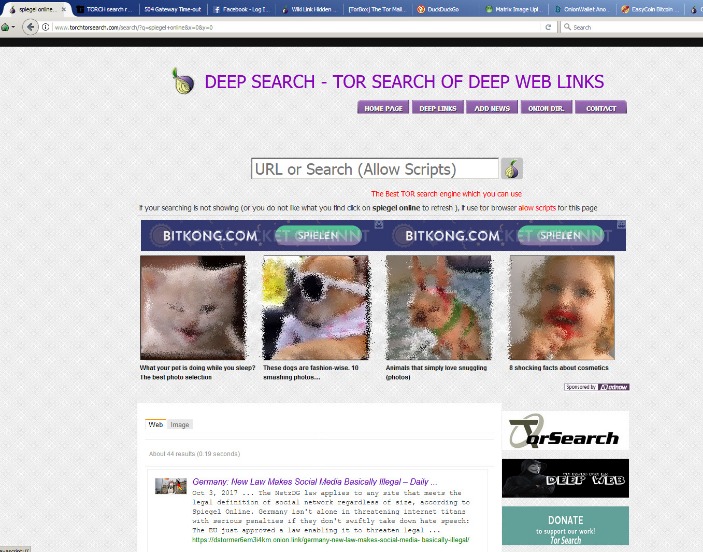
Keep reading for a rundown of the best dark links you might want to check out. In Grand Theft Auto Online, players who purchase warehouses and garages for illicit cargo and stolen cars can buy/steal and sell them through trade on the “SecuroServ” syndicate website. One of the central76 discussion forums was Reddit’s /r/DarkNetMarkets/,777879 which has been the subject of legal investigation, as well as the Tor-based discussion forum, The Hub. Here you will get Carding, Counterfeit Money, Drugs, Electronics goods, gift cards, PayPal Accounts, and other services. The main purpose of UnderMarket is providing a Multisig Escrow service along with a list of vendors with products and reviews.
All of this underscores Riseup’s prioritization of users’ rights over business interests. Not to be confused with the riskier Hidden Wiki page, Wikipedia on Tor serves as a vast repository of information. You’ll find articles on a wide range of topics, such as history, science, and culture — and that’s just scratching the surface.

While this may all sound sophisticated, it is a financial crime and very risky. Those who use these services can still be traced and prosecuted if caught, especially as law enforcement continues to sharpen its tracking tools. Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit. Some marketplace operators first build trust by running a legitimate platform. Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content. The markets often share materials related to child exploitation, pornography, and non-consensual recordings, all of which are serious crimes that inflict lasting harm on real-life victims.
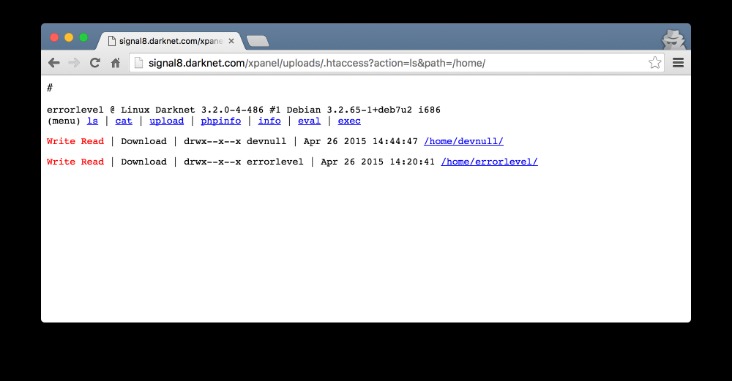
Despite its name, the marketplace operates primarily in English and serves a global audience. It has gained a reputation for being a reliable source of high-quality data for cybercriminals. It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals. Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info. And then there’s malware—click the wrong link or download the wrong file, and your device could get infected.

Other Privacy Tools And Services
As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms. Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. But these efforts of law enforcement don’t go in vain; hackers and criminals lose trust if a website or marketplace goes down.
The Top 10 Darknet Marketplaces Of 2025
Connecting to Tor first and then a VPN is generally not advised. This sequence offers less anonymity because your real IP address is still partially exposed along the Tor path. Plus, it’s slower since your data travels through the same four steps – entry node, relay node, exit node, and then the VPN server. All you need to do is click connect and you are officially connected to the Tor network and can now access dark web websites.



