Versus Market allows users to leave detailed reviews, making it easier to identify trustworthy vendors. Markets that lack proper security often become targets for law enforcement, scammers, or cyberattacks. High-volume vendors launch standalone shops using Tor and Monero, reducing dependency on marketplaces. This article reveals the top 10 dark web markets dominating in 2025, their unique characteristics, and the critical implications for enterprise cybersecurity. Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP.

Darknet Market List – Dark Marketplaces
- The site’s unique—loads fast, looks sharp, and vendors get treated right, keeping turnover low.
- Governments have become more efficient, using AI tools and blockchain analysis to deanonymize users, track crypto flows, and target market infrastructure.
- By creating hype around what is actually old – and probably irrelevant – data, cybercriminals can provoke publicity, generate buzz, and damage the reputation of both the supplier and its customers.
- With over 25,000 active users and a robust escrow system, Alphabay remains a benchmark for reliability and scale.
It also masks your IP address, making it difficult for government agencies to monitor or track your activities. We recommend using NordVPN as it offers top-notch security features, including dark web threat protection. According to researchers, hundreds of micro-markets sprang up in private channels. Analysts noted that Telegram enabled a shift toward decentralised “broker networks,” where smaller groups coordinated sales of Genesis-style data. This decentralised model makes it far more challenging to target with a single operation.
DPRK IT Workers Using Code-Sharing Platforms To Secure New Remote Jobs
Their DeadDrop system and wallet-less payments mean no one’s running off with your cash—perfect if you’re paranoid like me after a bad deal once. Listings aren’t public, but it’s steady as heck with 2FA and top-shelf encryption. They’re hinting at going decentralized in 2025—less downtime, more trust, right in line with the decentralized trend.
Social engineering attacks leverage trust, fear, curiosity, or urgency to trick users into revealing sensitive information, transferring funds, or compromising their anonymity. By learning to recognize these ploys and adopting defensive habits, you can significantly reduce the risk of becoming a victim. By exploring these categories of resources, users can discover that the dark web’s landscape is more nuanced than popular portrayals suggest. Education, activism, journalism, and creativity all find refuge here, protected by layers of anonymity. However, it’s vital to approach each new platform with caution—vetting its authenticity, reputation, and purpose before fully engaging. Armed with knowledge, critical thinking, and robust security practices, you can uncover meaningful, valuable content that challenges the dark web’s often one-sided reputation.

What’s The Benefit Of Escrow Systems?
While it has legitimate uses, it’s also a hub for cybercriminals, hackers, and other threat actors. For example, the CIA has a dark web site for anonymous reporting services. Plus, dark web search engines can also allow political dissidents to bypass government censorship, or for journalists to safely engage with whistleblowers. While it can be used for illegal activities, there are also perfectly legitimate forums, social networks, and communities. Crypto-laundering threat actors specialize in stealing and hiding the origins of their cryptocurrency.
II Security And Anonymity On The Dark Web
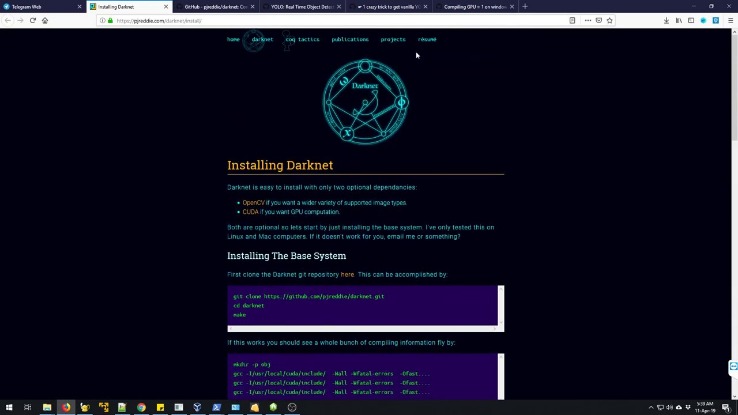
Monero, in particular, has become the preferred cryptocurrency on the dark web in 2025 due to its advanced privacy mechanisms, which obscure transaction histories and wallet balances from public view. However, you can trace its roots to the development of technologies like the Tor network or Freenet. In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet. This was the initial framework for anonymous communication and file sharing. Later in 2022, the US Naval Research Laboratory built on Freenet’s idea to create a secure and encrypted network for sensitive communications, which was later released to the public as open-source software.
While accessing the dark web may be perfectly legal in some regions, other places may restrict or scrutinize such activities more heavily. Engaging with certain types of content—such as copyrighted materials, illegal drugs, or illicit services—can lead to serious legal consequences. If you’re unsure about the legal boundaries in your country, consulting a knowledgeable attorney or reviewing reputable sources of legal information is a prudent first step. The return or influx of cybercriminals to dark web forums is expected to intensify competition among these resources. To stand out and attract new audiences, forum operators are likely to start introducing new features and improving conditions for data trading.
How Do I Verify Onion Links?
Established in 2019, Russian Market is a well-known and highly regarded data store on the dark web, specializing in the sale of PII and various forms of stolen data. Despite its name, the marketplace operates primarily in English and serves a global audience. It has gained a reputation for being a reliable source of high-quality data for cybercriminals.
Onion Links: The Hidden Side Of The Internet
Today, Telegram channels, bot networks, and private groups have become the default infrastructure for criminal coordination. This shift has not only reshaped how operations are run but also how law enforcement approaches surveillance and takedowns. Laws pertaining to anonymity and the use of privacy-enhancing tools vary widely from one country to another.
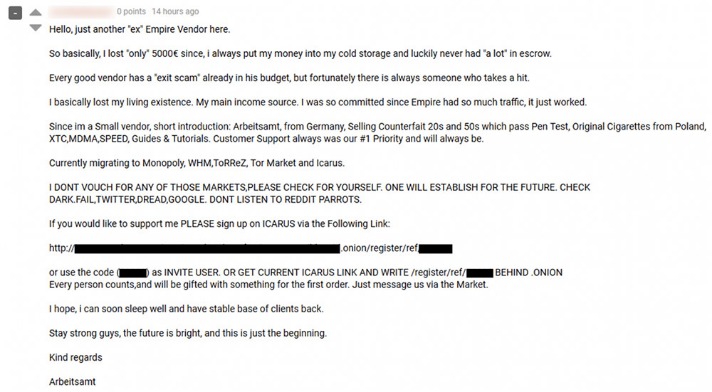
Some have left the space entirely, while others are demanding reputation-based systems and multi-layered escrow protections. The market is no longer about flashy interfaces or size—it’s about resilience, trust, and stealth. With $50M+ in monthly trades across our top 10, the stakes are high—scams cost $1M+ yearly, and 30% of links are traps.

Cryptocurrency Threat Actors
Instead of disappearing, Hydra’s network simply adapted to a new medium, underscoring the difficulty of suppressing illicit commerce with infrastructure takedowns alone. The region has seen an increase in these threats due to the current geopolitical situation, which is likely to continue to rise if tensions do not ease. Kaspersky Digital Footprint Intelligence data shows that in 2024 the number of Dedicated Leak Sites (DLS) grew 1.5 times compared to 2023. Despite this growth, the average number of unique posts per month has remained the same compared to the previous year. Cannaexpress is a cannabis‑exclusive bazaar boasting walletless Monero payments, smart PGP logins, a 5 % vendor commission and a polished modern UI.
It supports PGP encryption, two-factor authentication (2FA), alerts against fake sites (antiphishing), and a verification system for sellers. Its interface is easy to navigate, and it has a reliable escrow system, as well as allowing payments with Bitcoin and Monero. All of this has made it one of the most reliable markets still active in 2025.

Supporting BTC (60%) and XMR (40%), Torrez’s interface offers advanced filters and fast trades—90% complete within minutes—keeping prices 5–10% below premium markets. Vendors like “TorrezRx” and “HackElite” boast 98% ratings, with 94% shipping reliability. Launched in 2021, Torrez surged post-Hydra, growing vendors by 200+ in 2025, and survived a 2024 DDoS attack with enhanced defenses. Its top-tier rank reflects its vendor scale and trade strength, despite slight uptime and turnover challenges.
TorZon Market
Abacus Market was launched in 2021 and now lists over 40,000 illicit goods, including hacking tools, counterfeit documents, and listings for drugs. Darknet marketplaces remain central to illicit trade in 2025, with evolving business models, payment systems, and law enforcement responses. This survey highlights active and recently shuttered markets with actionable metrics and intelligence for threat hunters, CISOs, and red team leaders. Launched in 2020, Cypher Marketplace sells fraudulent documents, stolen credit cards, fake IDs, and malware.



