But accessing this hidden part of the internet safely requires reliable Dark Web search engines — tools that help you explore the darknet without compromising your identity or security. Dark web search engines are like the underground maps of the internet. They help users uncover hidden websites that regular search engines like Google can’t reach.
Top 10 Deep Web Search Engines
Out of the 10 sites shown on the first page for each search, there mostly are only 2-3 unique websites. Any search engine mentioned here is not to be taken as an endorsement. On the one hand, this is considered beneficial for people living under strict regimes where censorship is common. On the other hand, it can lead to trolling, the spread of misinformation, and unsavory comments that users wouldn’t be allowed to make on the surface web. This onion site was created as a place for whistleblowers to pass information to journalists. It is a safe haven where anybody with information can share it anonymously and without fear of being tracked.
Table Of Contents
This setup ensures anonymity while leveraging NotEvil’s privacy-centric, no-log design. By 2030, ethical debates over content moderation could split the ecosystem, with some engines (e.g., Torch) remaining unfiltered and others (e.g., NotEvil) adopting stricter policies. Users will need to navigate this divide, favoring open-source tools for transparency. NotEvil could integrate differential privacy techniques to share aggregate data, aiding researchers studying dark web trends.
- The dark web contains content that’s only accessible through networks like Tor.
- This can include the sale of drugs, weapons, stolen data, and counterfeit items.
- To make its journalism more accessible to readers around the world, the New York Times launched its onion service in 2017.
- PageOn.ai excels in generating conversational content tailored to your needs.
Enhance Your Security
Even the best privacy tools are only effective when patched against the latest threats. Not Evil is a dark web search engine specifically designed for “.onion” sites. True to its name, Not Evil distinguishes itself by not employing advertising or web tracking. In 2025, as privacy battles intensify, these tools are more vital than ever. Fire up Tor, choose your engine, verify your .onion links, and dive in—just keep your digital armor on. Engines like Ahmia minimize this with no-log policies, but misconfigurations (e.g., enabled plugins) or correlated metadata can expose users.
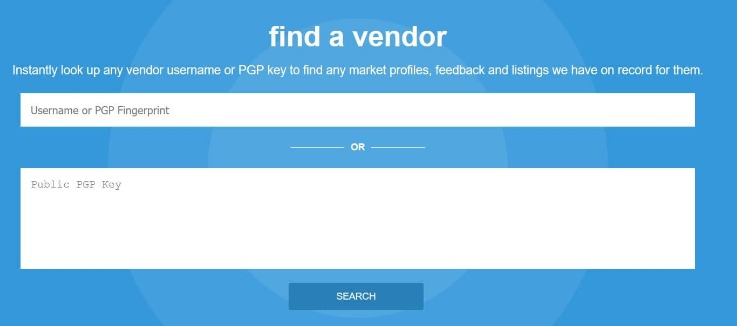
Recon is used to find information about darknet vendor profiles and monitor their activity. Yes, using a VPN along with the Tor browser enhances your anonymity and security. Designed to mimic Google’s layout, NotEvil gives safe, readable results. Some sites might use these details for advertising, analytics, or tracking your online preferences.
Filtering Of Illicit Content
Fake search engines usually give themselves away with poor design or broken functions. Many display endless ads, push suspicious downloads, or return results that seem irrelevant. If a search engine looks messy, slow, or overloaded with pop-ups, it is often a sign that it cannot be trusted. A real dark web search engine focuses on clean results and basic functionality. It does not try to be flashy, and that minimal approach works well in the Tor environment. Results load quickly, and users can jump between categories without much difficulty.
- When selecting a VPN, verify that it works smoothly with your browser and search engine.
- Instead, onion sites are derived from a cryptographic key and must be accessed using the Tor browser.
- Operating on a freemium model, users have the option to upgrade for an ad-free experience and access to features like historical website versions.
- I also recommend covering your webcam and disabling location services before accessing .onion sites.
- To navigate it safely, it’s crucial to use a reliable VPN, like Forest VPN, alongside the Tor browser to enhance your security.
This List Contains The Search Engines Most Requested By The Community On The Deep Web:
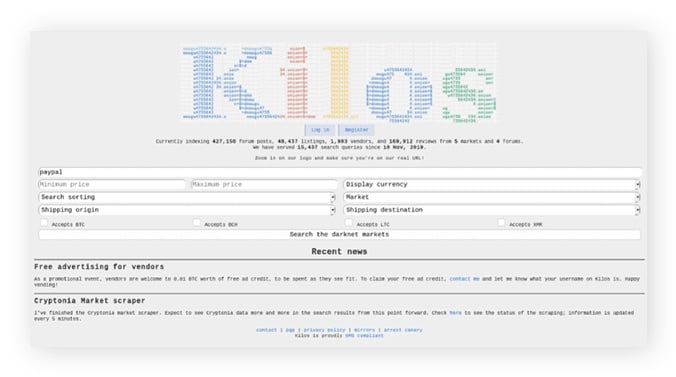
However, the majority of sites are hidden and sit in an online space called the deep web, where the darknet is only a small portion. Always run the latest version of the Tor Browser to protect against security vulnerabilities. Outdated versions may contain weaknesses that attackers can exploit to compromise your anonymity. I recommend enabling automatic updates and checking for new versions before each session. KeyBase combines encrypted messaging with secure file sharing and identity verification. Its dark web version provides the same functionality as the clear web option, while adding Tor’s anonymity layer.
Top 10 Dark Web Search Engines Of 2025 For Safe & Private Access
This particular search engine was built by Hugbunt3r, a prominent member of the popular Dread service on the dark web. However, speaking based on personal experience, its search results are not impressive. For instance, I wanted to know Twitter’s onion URL, a very simple piece of information. Yet, it reported everything but that showing how far these search engines have to go in order to improve. However, Ahmia, Torch, and DeepSearch are among the most commonly used options.
Set Tor Browser’s security level to “Safest” for critical dark web activity. This disables potentially dangerous features like JavaScript that could reveal your identity. NoScript and HTTPS Everywhere extensions provide additional protection against malicious scripts and unsecured connections. TorBook aims to be a privacy-focused alternative to mainstream social networks. It emphasizes anonymity while providing familiar social media features.
To reduce this risk, use the Tor Browser properly, keep your software updated, avoid sharing personal information, and pair it with a reliable VPN. Following best practices for online anonymity helps, but staying cautious is essential since no method is completely foolproof. Haystack doesn’t track or store your search queries or personal data, which is critical to maintaining anonymity on the dark web.
It contains millions of scientific research documents from around the world. The site seeks to liberate information by making it free to individuals and institutions. ProPublica is a popular online publication that won five Pulitzers in 2016. It aims to expose abuses of power and betrayal of public trust through investigative journalism. Moreover, due to its popularity, many copycats of the Hidden Wiki exist. So don’t be surprised if you encounter different versions that claim to be genuine, and be very careful.


Enable cautiously, as media can harbor malware; use antivirus and verify sources for cultural or research purposes without downloading untrusted files. They operate on Tor, encrypting queries end-to-end, but users must still enable “Safest” mode and use VPNs to prevent leaks. This makes them superior for privacy advocates, though opaque operations in some (e.g., Torch) can raise concerns.

They can be easily traced and even prosecuted if they share the information on the surface web. SecureDrop is a site that protects the privacy of journalists and whistleblowers. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired.
The search engine doesn’t impose censorship, meaning you can find a broad spectrum of sites, including those that may be illegal or disturbing. TorlanD opens up access to a vast range of hidden content, allowing you to navigate the deep web freely without restrictions. Deep Web search engines have been around for a while, but they’re usually not recommended because of the security and privacy risks involved. But there are some safe and secure ways to use these engines without having to use the TOR browser. How hidden web search engines work is by using a special algorithm to index hidden content.



