
Multi-signature escrow and real user feedback make it trustworthy. For 2025, they’re tweaking the mobile site, which I’ve been wanting forever—makes it easier on the go, especially if you’re using Tor on your phone (see how). It’s not fancy, but it’s dependable, and that’s why I keep coming back. Incognito’s all about keeping things easy and safe—perfect if you’re avoiding street buys.

The New York Times
Your data is encrypted in the Tor browser before reaching the ZeroBin servers. This service is a good source of statistics if you have a school project requiring research on Tor and the dark web. However, note that the site only uses non-sensitive and public data for the metrics. The Tor Metrics is a good place to get more information about the Tor project.
What Are Onion Sites?
Monero, in particular, has become the preferred cryptocurrency on the dark web in 2025 due to its advanced privacy mechanisms, which obscure transaction histories and wallet balances from public view. Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users. Saheed Aremu passionately advocates for digital privacy and cybersecurity in the modern digital age. As one of PrivacySavvy’s resident VPN experts, he guides readers on protecting their online information and anonymity.

Legal Repercussions Of Using Dark Web Markets
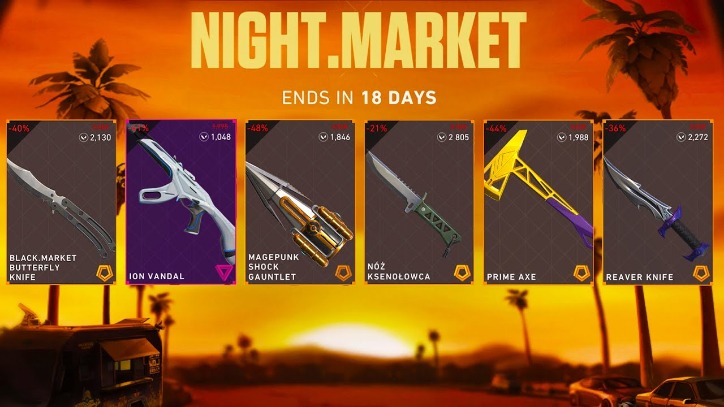
There’s much more to learn about the dark web, but here, we’ll focus on listing the best .onion sites you won’t find on Google. Silk Road was one of the first darknet markets, but in 2013, the FBI shut it down. Its founder, Ross Ulbricht, was arrested, and law enforcement took control of the site. Since then, many copycat markets have tried to replace it, but not all of them have lasted. The key differences between dark web markets and regular online stores are clear. Regular stores are public, with visible ads and a standard payment process.
- By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet.
- Participating in an online black market comes with a range of significant risks.
- Email is one of the least secure communication systems; the email providers have access to the contents of your inbox.
- AlphaBay was one of the most popular and largest dark web marketplaces before it was taken down by law enforcement in 2017.
Best Black-Owned African American Website Design Services Of 2025

The great thing about sharing via the Dark Web on SecureDrop is that users can do so without fear of persecution and without the possibility of being tracked down and punished. With this in mind, it is essential that you are careful about what you choose to visit and where you choose to click. As always, we strongly recommend using a reliable antivirus and a robust VPN to increase your security. For this reason, it is always better to use a trustworthy VPN for Tor while accessing the Dark Web, as this will provide a robust additional layer of privacy. First, check out our beginner’s guide on how to use Tor, then come back when you’re ready to get started.
Set Up Tor Browser
While it’s a deep resource, it’s also illegal in many countries, because it may violate copyright restrictions, so check out the laws in your area before visiting. Background research tasks included learning from past drug lords, researching legal matters, studying law enforcement agency tactics and obtaining legal representation. Patterns recommended to avoid include hiring hitmen like Dread Pirate Roberts, and sharing handles for software questions on sites like Stack Exchange. Taking the necessary precautions makes tracing your activities on the dark web difficult.

First Deep Web Black Markets
Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. Think of Tor as a regular browser like Firefox, Google, or Safari.
Data breaches like the ones mentioned above highlight the significant threats posed by dark web black markets. Stolen data can quickly transition from legitimate systems to underground forums, where it becomes a valuable commodity for cybercriminals. To counter these risks, organizations need robust, proactive solutions that go beyond traditional cybersecurity measures. This is where Brandefense’s Dark Web Monitoring Solution plays a critical role. Monero and Bitcoin are two of the most commonly used digital currencies on the dark web markets.
The layers of encryption hide your data and activity from snooping eyes. It allows vendors to sell without registration, which provides an added layer of anonymity, making it one of the more flexible and user-friendly markets on the dark web. Given the explosive growth of these markets, organizations must prioritize proactive threat monitoring.
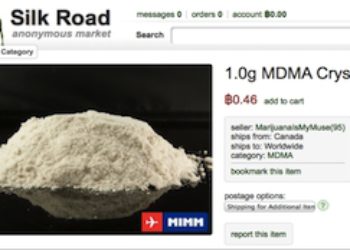
Dark web listings surfaced almost immediately after the breach, advertising this information for sale to cybercriminals. Even after Silk Road went down, dark web marketplaces haven’t slowed down. Stopping their growth takes serious effort from US agencies like the FBI, often working hand-in-hand with international law enforcement. The site gives out free samples of the stolen data every now and then to gain more customers.
Top 5 Deep Web Black Markets
For this reason, you must watch out and avoid opening anything that looks suspicious to you. Immediately close your entire Tor Browser window (not just that active tab). Note that engaging with the content in any way is not only distressing but could also put you at legal risk. This is because law enforcement often actively monitors these sites.
- ActiveX and Java frameworks are susceptible to being exploited by hackers.
- Eldorado.gg has Candy Blossoms, Sunflowers, Dragon Peppers, Sugar Apples and many other kinds of Grow a Garden fruits available at any time of the day with delivery within minutes guaranteed.
- The quantity, price, and characteristics of the product are all provided.
- Not every visitor is a criminal, but this is where most cybercrimes begin.
If you fall for it and log in, they immediately steal your credentials and either sell or use them for other scams. The fallout for victims whose data is stolen and sold can be devastating. They suffer losses such as identity theft, financial loss, and emotional distress due to damage to their personal and professional lives.



