
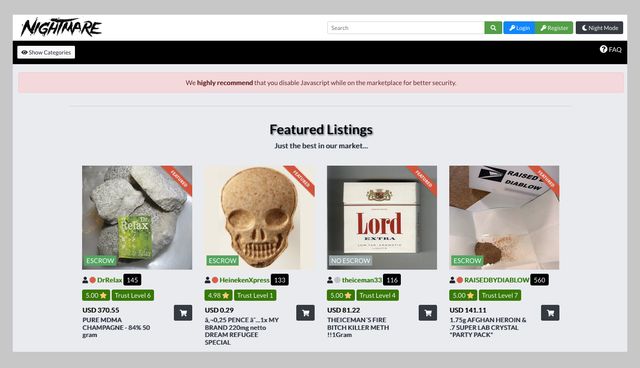
There are many fake marketplaces and platforms that might offer to sell you goods or services but actually take your money without providing anything in return. Since the dark web is unregulated, there’s almost nothing scam victims can do to seek justice or compensation. Sites often have simple black or dark-themed backgrounds and minimal design elements. Before we look at how to access the dark web, it’s important to have a thorough understanding of what it is, as there are many misconceptions about it.
Major Risks And Downsides
If you are a journalist or whistleblower and want to access the dark net for legal purposes, this guide is for you. We have covered some in-depth and tested steps to use it safely. Accessing the dark web sites isn’t safe and requires a user to go through several privacy measures to access it anonymously. With solutions like Dark Web Monitoring, Threat Intelligence, and Threat Detection, Brandefense empowers users to detect threats early, respond proactively, and safeguard their digital assets.
PRIVACY ALERT: Websites You Visit Can Find Out Who You Are
If you are in a position to report the incident safely, you should report it to the authorities immediately. It’s recommended not to be too vigilant here and leave the investigation to the professionals. It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals. Overall, Subgraph OS is a secure and privacy-focused operating system well-suited for high-risk environments. Additionally, you can opt for Subgraph OS as a second option to Tor. The early version of Tor was created to mask spy communications.

What Is The Best VPN For Tor?
- Users also face the potential danger of government monitoring and surveillance — or scams and fraud, and other activities that can lead to financial loss and identity theft.
- Formerly, Darren served on the Committee of Technology Infrastructure under Mayor Richard Daley.
- The affiliates distribute the ransomware packages through the dark web.
- Also, since the Tor Browser is based on the Mozilla Firefox platform, it’s susceptible to the same attacks that other browsers are.
- NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites.
- A VPN will mask your location and stop the online breadcrumbs that can lead back to you.
A step-by-step guide to safely accessing the dark web while maintaining your anonymity and security. If your personal information has been leaked on the dark web, your risk of identity theft and financial fraud significantly increases. This is why many people prefer an identity theft protection service and a financial and credit fraud protection solution.
Step-by-Step Guide: How To Access The Dark Web Using Tor Browser
From data breaches to counterfeit products and unauthorized brand use, malicious actors exploit the Dark Web’s anonymity for financial and reputational harm. Some dark websites offer hacking services, such as password cracking and DDoS attacks, for a fee. After connecting to the Tor network, the Brave browser in the bottom left corner, “If your personal security depends on staying anonymous, use Tor Browser instead.” gives a warning. The free version also includes basic malware protection, which is a nice bonus considering how sketchy some dark web sites can get. Hotspot Shield’s free version gives you 500MB of data per day, which resets every 24 hours. During our testing, we ran Tor over Proton VPN on both desktop and mobile.
BBC Tor Mirror

Yes, Tor offers a portable version that can run from USB devices. Secure communication for journalists, accessing privacy-focused forums, and whistleblower submissions. Tor encrypts your traffic and routes it through multiple volunteer-operated relays, making it difficult to trace. Text message spam isn’t just annoying—it’s a potential cybersecurity threat. Ever tried to connect to Wi-Fi and seen a prompt asking for a “network security key”? Yes, many organizations monitor the dark web for cybersecurity intelligence—always in line with legal compliance.

Hacking And Cybercrime Services
In some parts of the world, simply using a browser like Tor can get you flagged by these agencies, even if you don’t partake in illegal activity. Venturing into the dark web with your phone is a journey into a lesser-known internet space. By equipping yourself with the right tools like Forest VPN and Tor or Onion browsers, you can explore safely and securely. Remember, the dark web isn’t just a den of iniquity; it’s a haven for privacy and free expression. Whether you’re a journalist, an activist, or simply curious, take the necessary precautions to remain secure.
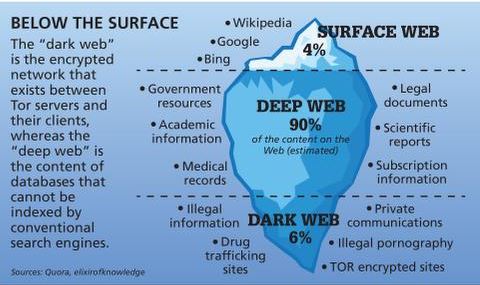
However, it is estimated that the dark web makes up only a small fraction of the overall internet, likely less than 0.01% of the total content. That said, if you’re serious about staying secure and anonymous long-term, NordVPN is clearly the best VPN for accessing the dark web. With long-term plans starting at just over $3/month, it’s also one of the most affordable ways to get premium-level privacy while browsing the dark web. That means you can access .onion sites without even opening the Tor browser. For deeper access or full Tor anonymity, you can also stack NordVPN with the Tor browser for double encryption, and during testing, everything stayed stable. These are the final stops in the Tor relay chain before your traffic hits the open web.
- You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe.
- They are only accessible through Tor, and they are a part of the deep web.
- Plus, the ISP won’t see that you’re using Tor, which is excellent.
- Without a VPN, your ISP or network administrator may be able to detect, monitor, or block dark web access; Tor-over-VPN provides an extra layer of privacy.
- The dark web refers to content on the internet that is intentionally hidden and requires special software like Tor Browser to access.
However, the dark web is known for hosting illegal activities, such as drug trafficking, weapon sales, hacking services, and child exploitation, among others. The dark web, on the other hand, is a small portion of the deep web that is intentionally hidden and can only be accessed using special software or configurations, such as the Tor network. The dark web includes various illicit activities, such as black markets, drug sales, illegal pornography, and hacking forums.

Types Of Dark Web Sites (and What Really Goes On There)
Tor2Web is a rather popular proxy that works with the Tor network. All you have to do is replace “.onion” at the end of the onion URL with “.onion.to”, “.onion.city”, “.onion.cab”, or “.onion.direct” and you should be good to go. Tor stands for “The Onion Router,” and the Tor Browser is essentially a modified version of Mozilla Firefox with integrated scripts and other add-ons to protect your privacy. The browser is preconfigured to connect to the Tor Network and mostly works independently. Gannicus Oliver is an experienced tech journalist (he loves writing on emerging techs and digital privacy issues) and an online business consultant. In his free time, Gannicus enjoys uncovering thrilling adventures and traveling around the world.
Cloudwards.net may earn a small commission from some purchases made through our site. The editorial team did not participate in the creation of this guide. Gizmodo may earn a commission when you buy through links on the site.
Just for laughs and giggles, we visited this random pug’s ultimate guide to the dark web. You’ll notice that some websites’ loading times are longer when using Tor. If someone’s caught buying or selling illegal items like credit card numbers or hacked data, they can face serious federal charges—even if it all happened behind an anonymous screen. From real-time alerts vetted by Cyble’s Security Operations Center (SOC) to AI-driven risk tagging, Cyble enables faster, more informed response decisions. Its deep insights into cybercrime forums, compromised card databases, and exposed assets give security teams a critical edge.



