Note that Tails’ installation package is the .img format, which means that you’ll need software capable of burning images on your thumb drive. I strongly recommend surfing on the dark web using virtual machine software instead of your locally installed Windows. Because it’s easier to contain malware in a virtual environment, which can be fully controlled. Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. PCMag is obsessed with culture and tech, offering smart, spirited coverage of the products and innovations that shape our connected lives and the digital trends that keep us talking.
What Are The Best Privacy Tools For The Dark Web?
But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web. As mentioned before, your ISP and government institutions are not able to see what sites you visit on the Tor network, but they can probably see that you use Tor. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose. The content of all these pages is stored on Google’s servers, but it’s mostly outdated, old content; smartphone app content; journals; court records; private social media profiles, and much more. By using Tor and a reputable VPN, along with being careful and having the right tools, you can browse the dark web legally and safely.
Getting Started With Tor Browser
It also prevents your IP address from being collected by cybercriminals on the dark web (this can happen if your traffic goes through a Tor server run by bad actors). The VPN changes your IP address, and, if you activate it before you even access Tor, you’ll be entering the network with the VPN’s IP address (this method is called Tor over VPN). Aside from government agencies, other entities, including corporations and hackers, could potentially monitor and track your movements across the dark web. Again, they can use various tools and technologies for this, like tracking tools or social engineering techniques. This is another reason it’s best to use a VPN and be careful on the dark web to preserve anonymity. As a general rule, never download anything at all from the dark web.
The dark web has no shortage of criminal activity, scams, phishing sites, suspicious links, and malware designed to trick newbies. And because there’s very little use of HTTPS on the dark net, verifying whether or not a website is genuine using an SSL certificate is not feasible. If you want to use Tor privately, you can use either a VPN or Tor Bridges (Tor nodes that are not publicly indexed).
If you need a way to organize as an activist or you want to discuss censored topics with others, my first suggestion is to stick to offline meetups. The second, less secure option is to use encrypted messaging apps with ties to specific non-profit or activist organizations. For example, Briar is an extremely private chat app designed to help journalists communicate anonymously with sources. Signal is our Editors’ Choice for private messaging apps because it does a great job of blending privacy and social media functionality for a highly customizable chat experience. Kurt Baker is the senior director of product marketing for Falcon Intelligence at CrowdStrike.
Can I Get In Trouble For Accessing The Dark Web?
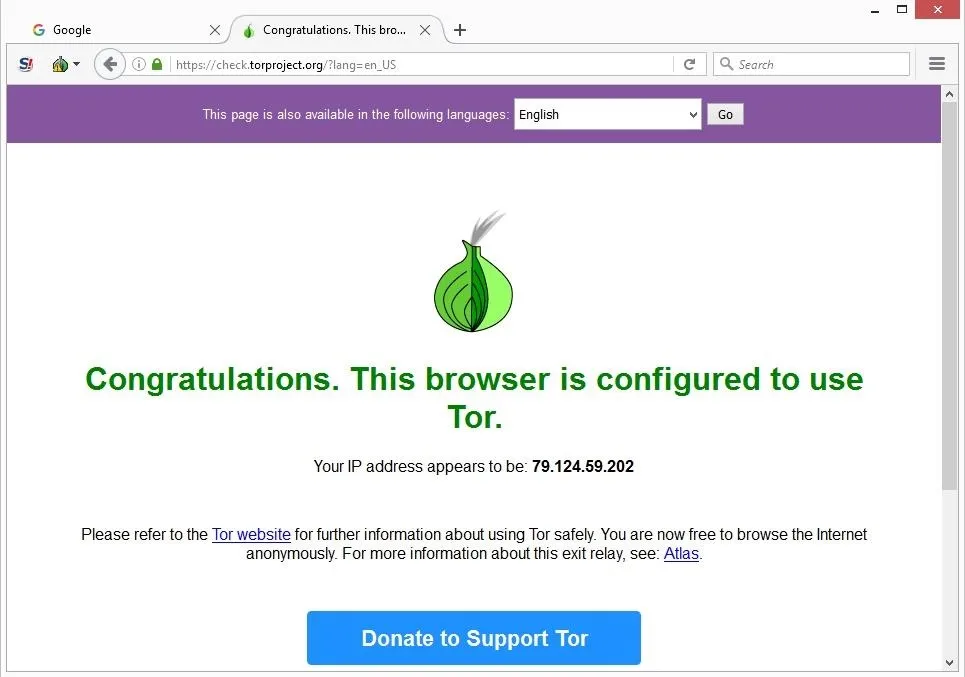
Other users appreciate the browser as it allows them to circumvent censorship. And yes, unfortunately, those seeking to perform criminal acts also use it. When using Tor, your traffic will never reach its intended destination directly, as it would on surface web browsers. Instead, it is funneled through different ‘nodes’ – other user’s computers – before coming out the other side.
Do I Need A VPN To Access The Dark Web?
This is why many people prefer an identity theft protection service and a financial and credit fraud protection solution. By doing so, early signs of fraud can be detected in near-real time, such as new inquiries on your credit file like new credit cards or bank loans. Although browsing the dark web is not illegal, it contains unsavory activities that can expose you to danger.

Choose A VPN
We strongly advise against accessing the dark web, even for ethical purposes, unless you’re fully informed about the dark web risks and have enhanced your device’s security. When you visit dark web sites, even if you don’t have any ill intentions, you support the dark web ecosystem, which serves as a medium to conduct various illegal activities. As dark web websites are not moderated, they can host a wide range of malware, such as ransomware, keylogger, and remote access Trojan.
Risks And Threats On The Dark Web
The dark web, by contrast, is a deliberately hidden subset that requires specialized software such as the Tor Browser or I2P to reach. Instead of standard URLs, it uses non‑indexed domains like “.onion” and routes every connection through multiple encrypted relays to mask both server and user identities. That anonymity empowers political dissidents, whistleblowers and investigative journalists, but it also shelters ransomware gangs, contraband markets and extremist forums. In addition, know that while accessing the dark web is legal in most countries, engaging in illegal activities (buying or selling contraband, hacking services, etc.), is illegal everywhere.
- Staying anonymous requires continuous learning, self-awareness and legal caution.
- Using a VPN (Virtual Private Network) in tandem with the Tor browser ensures an added layer of security by encrypting your traffic before it reaches the Tor network.
- By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP.
- Here’s a look at several of the illegal items you can buy — with prices — courtesy of Privacy Affairs’s Dark Web Price Index 2023.
- The technology behind this anonymous connection is known as “onion routing,” which utilizes a layered approach to obscure data and protect users’ locations on the network.
Tor, designed by mathematician and computer scientist Roger Dingledine, along with two colleagues, emerged as an open-source project in the early 2000s. The dark web is notorious for hosting a wide range of cyber threats that pose significant risks to individuals and organizations. One common threat is the sale of stolen credentials, including usernames, passwords, and financial information, which cybercriminals use for identity theft and fraud.
Minimize Or Rescale Your Tor Browsing Window
For totally hiding all of your online antics, you’ll want to also use a VPN. Just remember, both the Tor Browser and VPNs will slow things down, so you’ll likely not be happy with streaming through the Tor Browser. Live OS options that can be run on nearly any computer by simply popping a USB stick in and booting from it include Subgraph OS, Freepto, and Tails. Other options are the Freenet and I2P (Invisible Internet Project) peer-to-peer networks, both of which provide censorship-free communications.
Examples Of Legal And Useful Dark Web Content
PIA is popular in the USA because it offers servers in all 51 states. People in the United States and abroad can use it to venture into the dark web in privacy. With RAM-based servers in 90+ countries and features like WireGuard, IPv6 leak protection, and a kill switch, worries are over. These websites will now work without issues, as the VPN hides the exit node and makes your traffic look inconspicuous.
Protecting your personal information should be your priority when using the dark web. Don’t share sensitive details, such as your name, address, phone number or financial information, with anyone. Doing so could lead to identity theft or other forms of cybercrime.
The deep web is crucial for maintaining privacy and security online, as it keeps sensitive information away from the prying eyes of the public and search engines. While the term “deep web” might evoke images of hidden, secretive content, most of it is just routine data stored on private networks. The deep web includes any online content that lives behind a login screen, paywall or other access restriction and therefore remains invisible to search‑engine crawlers.



